


|
|
|
|
Our sponsors make financial contributions toward the costs of publishing Linux Gazette. If you would like to become a sponsor of LG, e-mail us at .
Linux Gazette is a non-commercial, freely available publication and will remain that way. Show your support by using the products of our sponsors and publisher. To subscribe to Linux Journal, click here.
|
 |
 The Answer Guy The Answer Guy |
 |
 The Weekend Mechanic will return. |
TWDT 1 (text)
TWDT 2 (HTML)
are files containing the entire issue: one in text format, one in HTML. They are provided strictly as a way to save the contents as one file for later printing in the format of your choice; there is no guarantee of working links in the HTML version.
Got any great ideas for improvements? Send your
This page written and maintained by the Editor of Linux Gazette,
Write the Gazette at
|
Contents: |
 Date: Sun, 01 Feb 1998 21:43:23 -0800
Date: Sun, 01 Feb 1998 21:43:23 -0800
From: Bradley Akey,
Subject: Creative Labs SB-16 & Sony CDU76E-S
I am attempting to install RedHAt Linux ver 4.2 from a Sony CDU-76E-S CD-ROm connected to a Sound Blaster 16 via an IDE interface at base io 0x1E8, IRQ 15. Waht is the correct boot parameter to get this CD-ROM to function properley
 Date: Tue, 3 Feb 1998 08:25:32 -0500 (EST)
Date: Tue, 3 Feb 1998 08:25:32 -0500 (EST)
From: Michael Stutz,
Subject: Help Wanted: recording audio data
Is there any way to read and save the data that is currently being played by the soundcard, regardless of the sound source?
(There is a program in alpha which does this called paudio, at http://web.syr.edu/~jdimpson/proj/. It creates a readable /proc/audio -- but I haven't yet gotten it to work with the OSS-compatible driver produced by the Linux Ultrasound Project which I use.)
Michael Stutz
 Date: Mon, 09 Feb 1998 14:18:49 -0500
Date: Mon, 09 Feb 1998 14:18:49 -0500
From: Todd Blake,
Subject: Help Wanted
I like most people am the only person to use my linux system at home. What I'd like to do is when my system is done booting to have me automatically login as my main user account(not as root though) on one virtual console(the first) and leave all other consoles and virtual consoles alone, so that someone telnetting in will get a login prompt like normal, just that I won't. I'd still like the other vc's have login's for others to login and other reasons. I've tried just putting /bin/sh in /etc/inittab and that didn't work, and I'm stumped. Does anyone have any ideas on this?
Todd Blake
 Date: Mon, 09 Feb 1998 17:47:08 -0600
Date: Mon, 09 Feb 1998 17:47:08 -0600
From: peter smith,
Subject: Problems with Linux through Wingate Socks
I'm having a few problems accessing the internet through Wingate v2.0 on my Windows95 machine using my Linux Redhat 4.2 installation. I've had this SOCKS server set-up for quite some time on my internet dial-out machine and have previously had no problems accessing the internet through this server via my second machine's installation of Windows95 or even WindowsNT. The problem is directly related to DNS lookups. If I access a domain-name from my Linux machine that seems to get redirected, I will receive an error that the DNS address does not exist. For instance, if I attempt to open the web page http://www.kernel.org (which gets redirected to http://linux.kernel.org) my browser (Netscape v4.04 for Linux 2.0* i386 rpm) reports a DNS error. However if I instead attempt to open the redirected web page http://linux.kernel.org my browser will open it ok, without error. I'm baffled by this behavior and have tried a number of different things! I can provide more detailed information if needed. Thanks in advance to any who try to help! ;)
I love Linux Gazette and have a great time browsing all the cool suggestions and tips! Keep up the ideas and info!
PeterS
 Date: Mon, 09 Feb 1998 19:04:42 -0500
Date: Mon, 09 Feb 1998 19:04:42 -0500
From: Melmac88,
Subject: Shadow passwords
Can someone do a clear explanation on how to set up a shadow password file, and exactly how it works? I've seen this recommended for security purposes in many books and articles, but there never seems to be an explanation on how to do this.
 Date: Wed, 09 Dec 1998 04:38:06 -0900
Date: Wed, 09 Dec 1998 04:38:06 -0900
From: David Lev,
Subject: my dual pentium
My name is David Lev, I have a problem with my second CPU.
I am currently using a Caldera OpenLinux Standard with Kernel (2.0.29-2). After I install the system I try to enable the 2 CPU and my computer FREEZE or I loss my DeskTop and it takes for ever to do one process. but with one CPU the computer work fine no problems at all. I ask for your help. If you can help me also on how to enable 2 modems and run them as one.
My computer content:
ATX Dual Motherboard - GA-586DX with SCSI on board Adaptec 7880 CPU - 2x 233MMX Pentium 128M RAM EDO 2x 3.1G HDD - W.D - IDE 2x 8X CD-ROM - IDE 2x 56K Modem ESS Sound card
 Date: Sat, 14 Feb 1998 15:00:34 EST
Date: Sat, 14 Feb 1998 15:00:34 EST
From: Andreas M. Weiner,
Subject: Linux and AMD K6 Processor - any Problems?
This is my hardware configuration. Support answered that there would be problems with using the K6 with Linux; for instance a crash.
What dou you know about this problem ?
Could you send me a some informations to solve this problem ?
Are there Kernel patches available ?
I'm looking forward of getting the answers from you
Andreas M. Weiner
 Date: Sun, 15 Feb 1998 10:26:36 -0800
Date: Sun, 15 Feb 1998 10:26:36 -0800
From: David,
Subject: X without a Mouse?
Been searching around the net and ldp, and can't seem to find anything on this one. Trying to be able to use X WITHOUT a mouse. Yes, I know, it works bets with a mouse, but I'd like to be able to get at least limited x funcationality without it. Any help is greatly appreciated, and being waited. Also, is there any was to do mouse emulation without a mouse? I found a program that translated ps/2 to a standard serial mouse, for before x supported ps/2, i assume... anyone know if a program has been written to allow the keypad to do mouse, ie, translate keypad input to /dev/mouse? Thanks for your time, hoping some kind linux guru's out there can help. :)
David
 Date: Mon, 16 Feb 1998 21:59:04 -0700
Date: Mon, 16 Feb 1998 21:59:04 -0700
From: Todd Jamison,
Subject: Help with Sound Card
I currently am running RedHat 5.0 on a Pentium 150 W/48 MB Ram. I = cannot get my ESS ES1868 plug and play sound card to work. I am very = new to linux and am still learning. If anyone can help me i would = really appreciate it.
Todd
 Date: Tue, 17 Feb 1998 16:41:49 -0600
Date: Tue, 17 Feb 1998 16:41:49 -0600
From: John Gorman,
Subject: HP4 & font
I just installed a HP LaserJet 4L on RedHat 4.2 Intel and when I print postscript (from emacs, etc), it prints at about a size 24 font. How to I set my font where I want it.
Thanks
John Gorman
 Date: Fri, 20 Feb 1998 08:46:12 +0100
Date: Fri, 20 Feb 1998 08:46:12 +0100
From: Jeroen Bulters,
Subject: Changing XDM windows
Can I change the XDM login window/screen? I have a cool house logo so i want to use it in my own Home Network. And at my school they want to know to so. Is it possible. If yes, how? If no, WHY NOT.
Jeroen Bulters, The netherlands
 Date: Tue, 17 Feb 1998 01:36:30 +0000
Date: Tue, 17 Feb 1998 01:36:30 +0000
From: Mackenzie St. Louis,
Subject: New Motherboards
A lot of motherboards have been coming out lately with built in graphics and sound. Any plans to cover them. I just bought a TX-Pro-II board with graphics and sound. However I think I will be returning it since I can't get the sound to work. It has a SoundPro chip. Can not also get XFree 3.3.1 to run properly. It will only come in 8 bit 320x200, even though the graphic chip is supposed to be AGP. If you could point out where I can get some info. I would gladly write an article for the Gazette in case any else comes across this same problem. Please email me with any info or questions.
 Date: Tue, 24 Feb 1998 16:28:09 -0800
Date: Tue, 24 Feb 1998 16:28:09 -0800
From: chewey nougat,
Subject: HELP-Installing Linux on a FAT32 Drive
I'm interested in installing linux on a machine I built recently, but = when I installed Win95(b), I idiotically opted to format the drive using = FAT32, which in a 95-only environment is great, but linux can't read it = for greek.
I've looked around for utilities to effectively un-FAT32 the drive, = which I will then partition with Partition Magic to use the freespace as = a native ext2 partition, etc., but am having little luck. Reformating is = a disheartening prospect I would rather not face, but am fully prepared = to do so if I don't find any help here.
much thanks,
nate daiger
 Date: Thu, 26 Feb 1998 13:47:06 -0500
Date: Thu, 26 Feb 1998 13:47:06 -0500
From: Brian O. Bush,
Subject: question on motor control
Does anyone know how to interface and control two motors from a Linux box? I am looking for a simple solution (in circuit at least).
Thanks,
Brian
 Date: Fri, 27 Feb 98 14:16:13 -0500
Date: Fri, 27 Feb 98 14:16:13 -0500
From: Bill R. Williams,
Subject: Wanting HELP!
First off: I can *not* believe I am the only one bitten by this.
In the process of getting a System installed I upgraded from the original CD-ROM install of (Intel) RedHat 4.2 to the new RedHat 5.0 CD-ROM. One of the significant items on this system is the mars-nwe Netware emulator.
Under the RedHat 4.2 with mars-nwe 0.98pl8-1 the mars package ran fine, but logged copious errors about there being "too many connections -- increase the number in config.h". But it ran, and I *liked* the way it happily did Netware duties! (Especially the printer part.)
The *new* RedHat 5.0 with mars-nwe 0.99pl2-1 offered some very desirable abilities, not the least of which is the move of some items (such as number of connections) to the run-time config file (/etc/nwserv.conf under RedHat, probably nw.ini on other distributions.) Now the bad news...
Of lesser, but still irritating, importance is the fact that the mars package won't shutdown without some hard kills. This may be related to the really important problem which is:
This new package spawns out nwconn processes with an empty parenthesis as the last token instead of the USERID ('nwconn ... ()') until all connection slots are eaten, and then, of course, will not recognize any new attempts. Any users already logged into the nwserv(ice) are Ok.
Since I am neither a Netware guru nor a mars guru I can only hazard a guess, but since the nwconn(s) are children of the ncpserv daemon I suspect that ncpserv is the source of the troubles.
I have tried every combination of parameter twiddling in the run-time config file that can think of, but to no avail.
One thing I have noticed, the 2.0.32 linux kernel /usr/src/linux/.config no longer has the 'CONFIG_IPX_INTERN' setting (should be unset according to mars-nwe docs) which existed in 2.0.27. This may or may not have anything to do with the problem. Checking the kernel sources, it appears that the RedHat rpm of the 2.0.32 kernel has the mars patches incorporated into the source.
Anyone who has solved this problem, please share the secret.
BTW: I attempted resolution through the RedHat Support system as a registered RedHat customer, and if anybody wants a good laugh I'll be happy to share the "circle of correspondence" from RedHat support. I did learn from the attempt that no *human* at RedHat actually ever sees the E-Mail to the support team or 'Bugs' team. (The "auto answer" mechanism will get right back to you, though, and tell you not to expect an answer.)
As I said, I can *not* believe I am the only one bitten by this, because I've looked on the news groups and seen several posts with "Mars and RedHat 5.0" in the Subject fields. These were all on the French os.linux.... lists, and unfortunately I do not read French!
Sorry for the rambling on...
Bill R. Williams
 Date: Sat, 7 Feb 1998 13:03:24 +0100 (CET)
Date: Sat, 7 Feb 1998 13:03:24 +0100 (CET)
From: Manfred Lemke,
Subject: Support for IBM Ethernet card?
I'm frantically searching for some kind of support for IBM's LAN Adapter/A for Ethernet. Does any of you know of a driver in the Linux Kernel that works?
Best regards and thanks in advance,
Manfred Lemke
 Date: Fri, 27 Feb 1998 00:09:33 +0100 (MET)
Date: Fri, 27 Feb 1998 00:09:33 +0100 (MET)
From: Radoslav Dejanovic,
Subject: Linux Journalists International
Linux Journalists International is an effort to make a meeting point for journalists who use Linux or simply write about it. It is also a place where other journalists and other people can take a look what is going on with Linux and media that supports it. There will be info pages about magazines/media and journalists who use Linux and/or write about Linux & related software.
I am editor in one croatian computer magazine (http://www.pcchip.hr) and this is my effort to give the Linux community something that lacks: popularity in media and a chance to boost media coverage of Linux. The homepage is at http://www.purger.com/~rado/lji.html - please take a look at it. LJ and LG are the strongest "Linux inside" media :), so your support in this project is essential.
Rado
 Date: Wed, 4 Feb 1998 10:02:08 -0500 (EST)
Date: Wed, 4 Feb 1998 10:02:08 -0500 (EST)
From: Paul Lussier,
Subject: Retraction Re: Linux and routing
It was just called to my attention that this came across a little to strongly and I'd like to clarify what I had previously written.
On Tue, 6 Jan 1998, I wrote:
Some words of caution. DO NOT HAVE YOUR LAN CONNECTED AT THE TIME OF THE CABLE MODEM INSTALLATION!!!! [Comapany names removed], and most of the other cable companies (we deal with them all here) will refuse to connect a LAN to their broadband network. Simply remove your hub or coax cable from view, and let them do what they need to do, then connect everything else up after they leave.
This was probably a little of an overstatement. I know only of 1 company that has this as a policy, but have heard of people having problems with some of the others. I have even recently been informed of one company that is *quite* Linux friendly and will "encourage the use of Linux as firewall/routers" as well as "allow and assist individuals & companies to setup there own Web servers, either at their permises or ours. We offer web hosting and will assist in registering a domain name". So, I obviously made an improper, blanket statement which does not represent the attitudes or policies of all companies.
Some other interesting tidbits of information about cable modems and cable companies:
1. Do not expect support for running a LAN over the cable modem from the cable company. They don't want you to do it, they won't help you do it.
2. Do not expect to put up a web server to be accessed by from the internet. You are a client, not a server. This technology,though fully capable of performing in this manner, is not being deployed for use this way.
Again, this is a blanket statement that *does not* apply to all cable companies. There is a good reason for those companies who do hold this policy, and perhaps I should have gone into more detail. When you get a cable modem from a cable company, *typically* you are agreeing to lease the equipment from them under similar agreement as you rent the TV set top box for cable television reception. The agreement typically states that you are not allowed to run the cable to any other TV for which you do not rent a box. The same goes for the cable modems. They are agreeing to lease you 1 modem for 1 computer. Setting up a firewall/proxy server to enable other systems access is exactly like placing a diplexor on you TV set, and running the cable to another television. That is a violation of the agreement, and is illegal, immoral, and unethical; it's stealing. And again, I re-iterate, this is not true for *all* companies. Check with your cable company, they should be happy to explain their policies to you.
I don't really think you *should* expect to be able to do either of these though, unless the cable company has provisions in place. You are agreeing to connect one computer to their network as a client. Anything more, you should expect to pay more, as they are providing you with increased capabilities. Just like the phone company charges more per added service (*69, caller ID, etc) so should the cable companies. Personally, I think that average rate of US$40-$50 a month for the equivalent of a T1 to my house is an awesome deal. If I want more capability, I should expect and be willing to pay more.
Cable companies WILL shut you down for running a server of anykind on your end of the network, and it can be *forever* :(
Again, I spoke without clarification. Obviously it depends upon the policies of your local cable company. I know of 2 or 3 instances where this has been the case. By stating the above, I was trying to warn of the possible consequences of violating the contract with the cable company. If the cable company specifies in the contract what you are allowed to do and what you are not allowed to do, you should expect to deal with the consequences of violating the agreement.
Spammers love cable/broadband networks. There have been several cases where a broadband network customer has been used by spammers and were subsequently shutdown for life by the cable company. What happens is the person decides to connect their private LAN to the cable modem but sets the firewall up incorrectly. Spammers search cable/broadband networks for proxy servers/firewalls (Usually Win95/NT) that allow incoming connections and then use that system to spam the entire cable/broadband network making the spam appear as if you sent it.
Spammers love any insecure system or network. Broadband Technology though, for the first time has allowed people more extensive and closer contact with other people on the internet. When you dial into an ISP with a normal modem, it's a little more difficult for devious minded people to take advantage of other users. But with cable modems, you now have hundreds and/or thousands of people all on the same private network, all with similars IP addresses, many of whom, now leave their systems connected for much longer periods of time. This makes it much easier for crackers, and other mischievous people, to take advantage of anyone who isn't running a properly secured system.
Usually you will be given 1 warning by the cable company, but there have been cases where none was given and the customer was completely shut down.I have heard of this happening on several occasions, where usually the person was running an improperly configured firewall, and spammers used their system to launch e-mail to thousands of people connected to cable companies' private broadband networks. If I'm paying $40 or $50 a month for this service, I, as a paying customer do not want to receive solicitous e-mail (spam) from some one else, especially if they are on the same broadband network as I. I would complain to my cable company about it and expect them to do something. It was these exact circumstances that has led to several people having their cable modems permanently removed.
Current modems are capable of transmitting at 10Mbs in both directions, but are usually deployed throttled back to a trasmit speed of 300Kbs and a recieve speed of 1.5Mbs. You want more bandwidth, they'll be happy to charge you more money :)
Personally, I think this is very fair. The cable companies are providing us with a service. We, as consumers, have to pay for this service. Just like my electric bill, if I use a lot of electric service, I pay a lot of money; or like the telephone company, if I have more features or want a T1, I pay more money than if I only had a normal telephone line. It's the same with cable modem technology, the capability is there for 10Mbps bandwidth in both directions. The technology is also there to regulate that flow. I expect the cable companies to use that technology. If I want LAN speeds to my house, I should expect to have to pay for it.
Again, I want to apologize for not clarifying my previous statements a little more. Please check with your local cable company before you do anything like connecting your private LAN to theirs. There are as many different policies as there are cable companies, so make sure to explicitly ask if what you want to do is permitted. This is a great technology and has tremendous benefits. Playing by the rules that the cable company has put in place will only help the technology spread. By violating the rules, you run the risk of losing access to it, as well as making it more difficult for the cable comapanies to contiue selling this service. Like any other market driven product, if there's no money in it, or it costs too much to implement, it will fall by the wayside, and no one benefits. By not folling the rules, we as customers can make it cost prohibitive for implementation, and conversely, by following the rules, we create more market demand, which in turn, continues pushing the technology forward, and everyone benefits.
#include <std_disclaimer.h>I don't pretend to know all the policies of all the cable companies. I don't assume to speak for any of the,, nor do I tell them how to operate. My opinions are my own, and no one else's. Dammit Jim, I am a Unix sysadmin, not a sales rep :)
Please feel free to send me questions, comments, criticisms, etc.
Paul
 Date: Thu, 5 Feb 1998 15:01:30 -0500
Date: Thu, 5 Feb 1998 15:01:30 -0500
From: Jack Chaney,
Subject: New Direction
I heard on the radio last night, an announcement that IBM has just successfully masked, produced and tested their newest piece of silicon. The processor is based on the PowerPC design and is reported to run at 1000MHz. Knowing what I know about the PowerPC and its various flavours, I think it would do to examine the idea of porting Linux in a native coded version to this processor platform. The pricing of this chip with a heavy duty operating environment could give the Alpha a real run for its money.
The PowerPC (for those who don't know) is a RISC based processor with three major operation blocks, each capable of independent operation. This enables the instruction flow to become parallelized so as many as three instructions can be done simultaneously, and because it is a RISC processor the instructions have been optimised so most occur in only one or two cycles. The other element of the design is to have an extremely large cache memory on-board the processor to reduce fetch time for instructions. To give an idea of the improvement in speed realised by this method, a PowerPC emulates the Intel part by keeping an interpreter block in the cache memory of the chip and interprets the Intel object code at comparable speeds of the Intel parts. The lure of creating a native Linux for this processor has crossed my mind on a number of occasions prior to the IBM announcement, and now I hope with encouragement this can move from fantasy to fact.
Jack Chaney
 Date: Fri, 6 Feb 1998 08:50:00 -0500
Date: Fri, 6 Feb 1998 08:50:00 -0500
From: Hampton, Mike,
Subject: Picking a nit
Maybe I should have called the subject of this "pet peeve" or something like that. What I am writing about is a simple grammatical error that I have seen many people make, but one that shouldn't appear in the Gazette or any published effort and that is the incorrect use of "it's" when the author should have used "its." An example is in the following sentence from a recent issue:
"This was necessary in order for a *nix version to behave to applications like it's counterparts so applications could run everywhere."
If you take the "it's" and expand it, the sentence would read:
"This was necessary in order for a *nix version to behave to applications like it is counterparts so applications could run everywhere."
The sentence no longer makes sense. Authors should remember that "it's" is a contraction of "it is." If they want a possessive of "it," they should use "its." I have also seen instances of authors using the apostrophe-s when they intended to form a plural but made a possesive instead (for example, using menu's, a possesive, instead of menus, the proper plural form). Like I said before, these are very simple and common errors, but ones which I feel can hurt the author's credibility.
Before anybody gets too defensive, let me say that as an employee of a major defense contractor, I have made the above error and have had it pointed out to me. Maybe that's why it stands out so much when I see it now.
Now I'll put down my pen and let others point out my errors.
Mike Hampton
 Date: Fri, 06 Feb 1998 08:12:09 -0600
Date: Fri, 06 Feb 1998 08:12:09 -0600
From: Tyree Gwyn,
Subject: love your site!!
i very much enjoy the information found on LG!! even though i am posting from a windows machine, i use linux(redhat 5.0) the majority of the time. i just happen to be at work, at this time.
anyway, being a newbie to this whole linux scheme, i have used your site, dejanews, oreilly books, and many howto's to get my system up to my specs. linux is very exciting, and has alot of promise. please keep up the good work.
Tyree
 Date: Sun, 08 Feb 98 17:34:41 -0500
Date: Sun, 08 Feb 98 17:34:41 -0500
From: Leon C. Isaacson,
Subject: Incomplete Book Reviews
In Linux Gazette 25, the review of "A Practical Guide to Linux" , by Mark Sobell, fails to supply the publishers name, publication date, and price. I enjoyed the review, but surely this information should be included as a matter of course. Given your reviewers laudatory comments, how or where can the rest of us hope to acquire this book?
Leon
(I agree. He should have included that information. Here's what I know:
Publisher: Addison Wesley Longman, [email protected], http://www.awl.com/
Price: $38.00 US
ISBN: 0-201-89549-B
-- Editor)
 Date: Fri, 21 Nov 1997 18:59:53 -0500
Date: Fri, 21 Nov 1997 18:59:53 -0500
From: Timothy D. Gray, Subject: Getting Linux to the public...
Has anyone noticed that when your friends see your neat-o Linux system with the nice 17 inch monitor, high quality video card, and fast computer that when they say, "Wow! that is nice, and you can do almost anything on that!" you cringe with the fact that they are going to want you to put it on their system? now mind you, I dont cringe on sharing the best O/S on the planet, In fact I want everyone to use Linux. It's just that almost all X windows software is written for 1024 X 768 or higher resolution video screens and that 99% of those wanting to use Linux and X windows only have a 14" monitor that can barely get past 640X480 at 256 colors. I tried several times to get friends into Linux and X but to no avail because the software developed for X is for those that have Gobs of money for good video boards and humoungous monitors. It's not a limitation of Linux or X, it that the software that is developed for these platforms are by professionals or professional users that can afford that new 21 inch monitor at the computer store. We as a group might want to see software scaled back to the 640X480 crowd.. then Linux would take the world by storm.. Until then It's going to be limited to us pioneers and Scientists...
Tim Gray
 Date: Wed, 25 Feb 1998 15:42:09 +0000
Date: Wed, 25 Feb 1998 15:42:09 +0000
From: Jaime E. Villate,
Subject: uptime record
In Issue 25 (February 98) Sean Horan wrote about a Linux system that ran continously for 274 days. Here is a quote from Bruce Perens (president of Debian, works at Pixar) that I took from http://www.debian.org
"I thought three months without a reboot was a big deal. When I mentioned it to our developers, one of them showed me details about his system. It was up for 458 days, and was halted to move it to another floor. The network and disk device drivers had handled tens of millions of interrupts in that time."It would be interesting to know what the record is for other operating systems older than Linux.
Jaime Villate, University of Porto, Portugal
http://www.fe.up.pt/~villate/
 More 2¢ Tips!
More 2¢ Tips! Apache SSL extensions...
Apache SSL extensions...From Frank: My problem is this one ... I've gone bananas in trying to find a document that explains how to install, in a step by step fashion, the Apache SSL "extensions" to one of my Apache WWW Webservers (the performance increase is awesome) can you or anyone that reads this help...
This is how I did it:
Glenn.
 Locate
LocateOne of my annoyances with the locate program have been that with it, users can see files they have no access to otherwise. So, I have deviced a little patch to the original sources to fix that, along with a few other annoyances. It inherently does a few other things as well. It will only list files that do currently exist (not just files that existed when updatedb was last run). Also, it adds the option -l to locate which simply performs a ls -l on the files returned.
To compile, get the sources from ftp://prep.ai.mit.edu/pub/gnu/findutils-4.1.tar.gz . Extract that, then apply the attached diff to it with: patch < locate.diff, and compile per the instructions within findutils.
The only file modified is locate.c, so you can skip the installation process if you already have updatedb/locate installed, and just simply replace your existing locate binary with the new one (keeping a backup of the original, should anything evil happen).
Enjoy
 Re: Printing Problems
Re: Printing ProblemsDate: Wed, 04 Feb 1998 22:05:40 +0100
From: M.H.M. Verhoeven,
Anyone that can help me. I'd love to hear it. I try running lpr, but everytime I get no name for local machine. How do I set this and/or what is the problem. -- Manish Oberoi
I had the same problems with printing (no name for local machine). You should put a entry for your machine in /etc/hosts, and your problem is solved. In my case, the name of my computer had changed, but /etc/hosts still contained the old name for my machine.
Gertjan
 Re: LG25, Netscape on the Desktop
Re: LG25, Netscape on the DesktopDate: Thu, 05 Feb 1998 00:26:03 +0100
From: Soenke J. Peters,
I use a similar trick to start up the browser-/mail-/news-window from three different buttons in my windowmanager's panel. For the mail-window, you have to start the script with 'mailbox:' as the url parameter, for the news-window simply use 'news:'. For urls beginning different from the above, netscape opens the normal browser window.
Soenke J. Peters, Hamburg, Germany
 RE: Linux and VAX 3400 and 3300
RE: Linux and VAX 3400 and 3300Date: Thu, 05 Feb 1998 10:11:00 -0700
From: James Gilb, To: [email protected]
I have just purchased a MicroVAX 3400 and 3300. I would like to put Linux on these two systems. Can you provide any help in this aspect.
I believe those are MIPS 3000 boxes, try the Linux VAX Port Homepage at http://ucnet.canberra.edu.au/~mikal/vaxlinux/home.html and the Linux/MIPS project at http://lena.fnet.fr/
My guess is that you will need to get your hands dirty on this one. You could also try NetBSD, they may have a port now.
If they are not MIPS boxes, then you could have a real challenge on you hands, but then isn't that half the fun of Linux?
James Gilb
 Binary File Access with dd
Binary File Access with ddDate: February 9, 1998
From: Leonard R Budney
dd stands for Disk Dump. Or if it doesn't it should. The "main" use for dd is to duplicate a floppy disk, bit for bit, to a file. You probably used it to create boot disks when you installed Linux for the first time, unless you used its much less functional cousin rawrite. If you're sick of keeping boxes of floppies around, you can use dd in reverse, and throw the floppy away. Depending on permissions, you might have to do this as root.
dd if=/dev/fd0 of=quicken_install_disk_1.img bs=1440k
The if argument specifies an input file (which defaults to the standard input). Naturally, the of argument names the output file (which defaults to the standard output). Finally, the bs argument tells dd what block size to use. Here we set the block size equal to the size of a floppy disk, and let dd read one block of data.
The man page says that the purpose of dd is to "convert a file while copying it." In English, that means that dd does not assume a file is made of text! It doesn't look for carriage returns to delimit lines, it doesn't stop reading at the first binary zero, nothing! This gives us the power to read files exactly, byte for byte. It allows us to read a fixed number of bytes, or physically to overwrite a file.
As just one example, consider /dev/random. That's a nifty Linux innovation--a pseudo device that accumulates randomness. Would you like to read 10 bytes of random data from /dev/random? It's a snap.
dd if=/dev/random of=/tmp/random.bin bs=1 count=10
Note that /dev/random provides binary data, so if we omit the of argument then that data will probably trash our display. Alternately, we could have omitted the of argument, but piped the output through cat -v to escape any non-printable characters. In addition to the arguments explained above, we use the count argument to specify the number of blocks to read. In conjunction with a blocksize of 1, count=10 tells dd to read exactly 10 bytes.
Here's a final example, for the paranoid. When you delete a file using rm, you only delete the inode pointing to your data. The data is still there, on the disk, waiting for somebody with a "Disk Doctor" utility to resurrect and read. Does that bother you? Well, you should delete your data, not just your file. Again, dd comes to the rescue. Normally dd truncates its output file before writing. The argument conv=notrunc overrides that behavior, and causes dd to write over any existing data. The following shell script combines all of these ideas, and wipes out your file by overwriting it five times with pseudorandom data, and then deleting it.
#!/bin/sh
FILE=$1
SIZE=`ls -l $FILE | awk -- '{print \$5;}'`
{
for iteration in 1 2 3 4 5
do
dd if=/dev/urandom of=$FILE bs=${SIZE} count=1 conv=notrunc
sync
done
} && rm -f $FILE
Enjoy!
Len.
 Follow-up to find 2c-tip
Follow-up to find 2c-tipDate: Tue, 10 Feb 1998 19:20:44 +0000
From: Markus Pilzecker,
in your December issue, one of the 2-cents about find had been:
A shorter and more efficient way of doing it uses backticks:
grep "string" `find . -type f`
Note however, that if the find matches a large number of files you may exceed a command line buffer in the shell and cause it to complain.
The solution to this is using xargs:
find <find_roots> <other_options> -print0 | xargs -0 grep <options>. xargs only puts as much onto grep's [or whatever else's] command line as fits without overflow. Only in the latter case will it start a new instance of grep. The trick of the first proposal to add ``/dev/null'' to grep's command line to make it print the name of the file in work is [mostly] superfluous then, since xargs [mostly] puts more than one filename onto grep's command line.
The find option ``-print0'' and the xargs option ``-0'' work together to assure correct handling of odd filenames.
Markus
 ispell & Pine 3.96
ispell & Pine 3.96Date: Fri, 13 Feb 1998 08:39:34 -0800 (PST)
From: Peter Struijk
To use ispell in Pine, go into Pine SETUP (press S, then C), search using WhereIs for "speller" (press W) and make sure the value set there is "ispell". That will do it.
Peter
 XVSCAN: Combining different parts together
XVSCAN: Combining different parts togetherDate: Sat, 13 Sep 1997 01:04:29 -0500
From: Earl Fryman,
To: [email protected]
Is it possible to combine two (or more) different parts from different pages on same fig? For example, if I scan pages and want to print transparencies from small part of the text enlarged. Now, if the part 1 is at the end of a page and the part 2 is on the following page, I have not been able to combine them on one single fig (part 1 and below it part 2). How could I do that with xvscan? If the parts are on the same page I have used cut, past and crop.
--
Juha Perkkio, [email protected]
Yes it is posible. Load the first image and select the portion of the image to cut. Press Alt-C (hold down Alt key and press C). Load the second image and press Alt-V. A frame window the size of the cut in the first image will appear. Position the frame where you want the image to be pasted, then press Alt-V (again). This even works if the two image are of different type (bmp, jpg, gif, etc.).
Earl Fryman
 2c-tip: Netscape on the Desktop
2c-tip: Netscape on the DesktopDate: Sun, 15 Feb 1998 19:43:58 -0100
From: Victor-A. Bruessow,
I'm using this little bash script to start Netscape:
#!/bin/sh if [ $1 ] ; then REMOTE_COMMAND="openURL($@,new-window)" else REMOTE_COMMAND="openBrowser" fi netscape -remote $REMOTE_COMMAND || netscape $@I think it has some advantages over the script from Tim Hawes:
 Linux and Win95
Linux and Win95Date: Wed, 18 Feb 1998 14:55:22 +1300
From: Justin Lodge,
Rexson Re: Your Question e-mail to Linux Gazette
Your big problem is that Win95 has probably helped itself to the entire drive already - so there is no space left available to install extra Linux partitions.
What you really should do first is to back up all the existing partitions using a tape or a Zip or a Jaz drive. Let me guess you don't have one of these..... if you can beg/borrow/steal one temporarily and back everything up before you do anything that would be good.
Maybe your D: partition doesn't hold much and you can transfer the data to the C: drive where Win95 is installed - this will allow you to re-use the D: partition for Linux.
Next - buy/beg/borrow/steal a recent copy of Red Hat for Linux (make sure you get the book and the floppy disks that come with the CD) and the Doctor Linux book.
Red Hat has a beginners book with it that explains a lot that you need to know to install Linux and a set of excellent scripts that lead you though the installation.
doctor linux has good beginners sections and more complex ones about dual booting Win95 and Linux
I would recommend that you DO NOT try to make the machine dual boot - it could cock-up the win95 installation but these articles will help you understand the mechanics around this area. The HOWTO articles in Doctor Linux are all available on the Internet if you don't want to buy a book but having a hard copy to reference is much easier.
once you have re-located any useful data off the D: to the C: then use the disk partitioning tool that comes with red hat to de-allocate the D: partition and then create the root, usr, swap and home (and any others) in this area. From memory I believe that the root partition has to be in a primary partition but all the rest can be logical partitions contained in a single "extended" partition.
This re-allocation of partitions is EXTREMELY dicey - make absolutely sure you understand which partition is C: and which is D: IF you de-allocate C by mistake then it is almost definitely un-recoverable unless you have Norton for Win95 or something similar that can repair the damage.
Create a boot diskette using red hat so that when you want to run Linux you just plug it in and re-boot the machine - booting off the floppy may seem awkward but it is much much faster than any version of Windoze.
Any one else using the family using the machine will not have this boot diskette and will not be able to see your partitions from Win95 and won't even know that Linux is there. This is how I keep my family off my copy of Linux.
Justin
 My $0.02 tip: Graphical su
My $0.02 tip: Graphical suDate: Wed, 18 Feb 1998 22:01:25 +0100 (CET)
From: Andreas Kostyrka,
Sometimes one want to do su but be able to use X11 programs like RH control-panel. There are several ways to accomplish this: *) The hard way: su - and copy&paste the xauth:
$ xauth list $DISPLAY # mark the output $ su - # xauth add <paste the above line> # export DISPLAY=<display mentioned in the pasted line.)
*) The overkill net way:
$ ssh localhost -l root
This depends upon you haveing installed ssh (ftp.replay.com is the site where one gets the crypto stuff for RH Linux in .rpms), and is probably not that fast, as it uses a X11 proxy forwarding server.
*) The graphical (XDM) way, or the way to show off for your WinNT friends:
$ Xnest :10 -query localhost &:10 must be perhaps customized if it is already in use. localhost is your xdm host. This should work if you use xdm for login. (==You have a graphical login screen.)
Andreas Kostyrka
 Easter Eggs in Netscape
Easter Eggs in NetscapeDate: Wed, 18 Feb 1998 13:32:57 -0800 (PST)
From: Eric Geyer,
I saw the list of Easter Eggs in Netscape, and I have two more, both much less useful than the ones you listed.
about:mozillaOn all the Unix netscapes I've seen, it changes the Netscape logo in the upper right.
about:jzwThis will take you to Jamie Zawinski's homepage, and will change the Netscape logo on Unix netscape except for version 4.
Just thought you would like to know...
Eric Geyer
 Core Dumps
Core DumpsDate: Thu, 19 Feb 1998 13:56:51 PST
From: Marty Leisner,
I was annoyed on Linux that file(1) couldn't tell what file dumped core if a core dump was seen.
For a while, I was doing strings | head and guess at it by inspection.
But size will do the job:
: leisner@dw;size core text data bss dec hex filename 45056 295036 0 340092 5307c core (core file invoked as minicom - dpp2)
marty
 |
Contents: |

 April Linux Journal
April Linux JournalThe April issue of Linux Journal will be hitting the newsstands March 6. The focus of this issue is Workplace Solutions with articles on Marketing Linux, WordPerfect 7, Satellite Remote Sensing, Linux in Biomedical Labs and much more. Check out the Table of Contents.
 Washington, DC Linux Users Group InstallFest
Washington, DC Linux Users Group InstallFest1 Feb 1998
On March 28, 1998, the Washington DC area Linux User Group (DC LUG) will have its next Linux Installation Fest. Volunteer experts from several local Linux user groups will assist computer users interested in trying out Linux, the operating system that Byte Magazine, Wired, PC Magazine and other industry publications agree is a significant software phenomenon. Bring your PC and leave with Linux co-installed, or just visit the demo room to see what Linux is all about.
Started as an exercise in Internet-based collaboration among hundreds of software developers around the globe, Linux has acquired a reputation for superior power and robustness, along with a relentless pace of improvements, a combination rarely matched by the mainstream software Unix and Windows NT industry.
Linux has attracted an estimated 3 to 15 million users, and also garnered commercial support, evidenced by several shrinkwrap vendors with shelf space in mass-market computer stores. Even though in most cases an installation of Linux is a simple procedure, DC LUG will help those who may have unusual configurations or simply some trepidations about jumping in. Representatives from RedHat Software, one of Linux vendors, will also attend and provide advice.
The InstallFest will be held at the Uniformed Services University of the Health Sciences, the medical school at the Bethesda Naval Medical complex, just inside the Beltway between Wisconsin and Connecticut Avenues.
Doors open at 10 AM through 4 PM, Saturday 28 March 1998. See http://www.tux.org/fest for details and a requested pre-registration form.
For more information:
David Lesher, , (301) 608-9775
Przemek Klosowski, , (301) 975-6249
 Linux in the News
Linux in the NewsLinux for Dummies by Jon "maddog" Hall and others and Linux for Dummies Quick Reference by Phil Hughes are out from IDG books. Get your copy today.
InfoWorld's 02/02/98 issue names Red Hat Linux 5.0 as it's OS of the year for 1997. The article can be found on-line at http://www.infoworld.com/cgi-bin/displayArchive.pl?/98/05/poy2a.dat.htm under the Operating Systems heading.
Red Hat's Press Release
 Debian Year 2000 Compliance
Debian Year 2000 Compliance1 Feb 1998
Debian's Y2K compliance statement is at http://www.debian.org/news.html#19980104
For more information:
Bruce Perens,
 "open source" -- new term for libre software
"open source" -- new term for libre software10 Feb 1998
The Open Source Definitionby Bruce Perens
Goodbye, "free software"; hello, "open source" by Eric Raymond
For more information:
http://www.opensource.org/
 Linux receives the Softwarove noviny "Product of the year" award
Linux receives the Softwarove noviny "Product of the year" award1 Feb 1998
Date: Mon, 9 Feb 1998 13:53:30 GMT
The Czech computer monthly "Softwarove noviny" awarded the Linux 2.0 operating system with its award "Product of the Year 1997". This award is regularly (for the sixth time this year) assigned to the best computer products available on the Czech market without any other limitation. The "Product of the Year" award is strictly non-commercial, no fee is paid and no application is put in. Among the criteria is technical excellence, amount of innovation, price / performance ratio as well as the amount of value added by the domestic vendor. The award was granted to 18 products for the past year, among them two operating systems.
Softwarove noviny (www.softnov.cz) is a prestigious Czech computer monthly. Its name (with meaning Software News) is rather traditional than descriptive: actually it is a generally oriented computer magazine that focuses on software as well as hardware, networking and other aspects of IT market. It is published in Czech language and distributed in both Czech and Slovak Republics. The Softwarove noviny reader?s group includes professional IT users, entrepreneurs and managers. The Softwarove noviny is the only Czech computer monthly prepared entirely from domestic sources without translated articles from American or German industry press. Softwarove noviny magazine publishes now 16,000 copies (total population of Czech Republic is 10 million), 85 % of which are paid (1/3 by subscribers). About 40 % of the magazine are occupied by advertisements of both Czech and worldwide IT companies. According the independent surveys from November 1996, the Softwarové noviny magazine is the most known IT magazine in the Czech Republic.
The WWW page of Softwarove noviny is available at http://www.softnov.cz/. The Czech Linux Users' Group has its WWW page at http://www.linux.cz/czlug/.
For more information:
Jan "Yenya" Kasprzak, , http://www.fi.muni.cz/~kas/
 WWW: inofficial StarOffice 4.0 for Linux FAQ
WWW: inofficial StarOffice 4.0 for Linux FAQ16 Feb 1998
Michael Hoennig has collected some questions and answers into an inofficial FAQ of Linux (and some UNIX-) specific topics of StarOffice 4.0. This FAQ in the German language can be found at:
http://www.on-line.de/~michael.hoennig/soffice4-linux-faq-49.html
This FAQ in an English version can be found at:
http://www.on-line.de/~michael.hoennig/soffice4-linux-faq-01.html
For more information:
Michael Hoennig,
 WANTED: Project LEAP: Linux-Equipped Astronauts Project
WANTED: Project LEAP: Linux-Equipped Astronauts Project1 Feb 1998
17 Feb 1998
Recent articles on the International Space Station (ISS) have mentioned that astronauts will be issued laptop computers running MSWin95. Other reports have predicted disastrous trouble with the station control software, because of poor engineering practices and unrealistic schedules.
This situation creates a real opportunity for Linux. While we (probably) can't help with the main station software, at least the astronauts can be freed from Win95 crashes. Imagine the sound bites: "At least our laptops don't crash all the time."
PEAL is a project to port the applications that the astronauts use to run under Linux, so each astronaut has a choice of operating systems. Many of them will continue using MSWin95, for a time, but if any astronaut chooses Linux, the others will begin to pick it up, just as happens on the ground.
Anyone who wants to take over the web page, design a project logo, set up a mail reflector, create a newsgroup, become group leader, or (almost forgot :-) port software, please write. We need to know what codes the astronauts need ported, and where the sources are. The project web page, for now, is:
http://www.cantrip.org/leap.html
For more information:
Nathan Myers, , http://www.cantrip.org/
 4th Annual Linux Expo, May 28-30th
4th Annual Linux Expo, May 28-30thFebruary 17, 1998:
Linux is making waves in the news, and now is the opportunity for the world to find out why. It's time to get ready for the largest gathering of the best and brightest minds in the computer world. For three business-centered and technology-packed days, May 28-30, the fourth annual Linux Expo will take over Duke University in Durham, North Carolina.
This year's Linux Expo is shaping up to be a can't-miss event. Visit the record number of Expo exhibitors (there is still time for your company to become involved) showing the latest in Linux-based hardware, software, and service solutions. And stop in on the business and technical discussions to hear talks by some of the most important names in technology today.
Yes, Linus Torvalds will be there. And so will many others.
Technical track speakers include:
There will also be Tutorial Sessions featuring among others:
Business track speakers include:
For more information:
http://www.linuxexpo.org/
 WWW: linux for starters WWW-page
WWW: linux for starters WWW-pageFri, 20 Feb 1998 08:29:00 GMT
Here's Yet Another Page Concerning Linux For Starters. In case anyone's interested... http://www.ping.be/leminator/leminator.htm
For more information:
Koen Janssens,
 WANTED: OpenBIOS - Freeware x86 BIOS iniatitive
WANTED: OpenBIOS - Freeware x86 BIOS iniatitive1 Feb 1998
Fri, 20 Feb 1998 08:42:53 GMT
Some discussion about the possibility of a freeware 'GNU' BIOS was casually mentioned on the Linux kernel mailing list last week. Talk about it escalated, and a mailing list was quickly formed. After a few more days of ideas, it seems like a very good possibility and some people just hell bent on getting started.
What we are looking for now are people with a high degree of knowledge about the low-level workings of the x86 PC architecture, and real mode programming experience. Please join the mailing list and offer what help you can.
Also understand that many Linux people are involved with this, but the purpose is a COMPLETE BIOS replacement for use with all Intel x86 OS's, not just some new boot loader.
To subscribe to the OpenBIOS Mailing list, write an email To: [email protected] Subject [leave blank!] subscribe [in the body] It is a majordomo managed list. Feel free to use extended MD commands as needed.
OpenBIOS web pages: (DO NOT expect to find much here yet! ) http://www.linkscape.net/openbios/
http://www.freiburg.linux.de/OpenBIOS/
For more information:
Dave Cinege
 Linus Torvalds at next SVLUG meeting March 4th
Linus Torvalds at next SVLUG meeting March 4th1 Feb 1998
20 Feb 1998
March 4, 1998, Linus Torvalds will speak at the Silicon Valley Linux Users Group (SVLUG) meeting. The meeting begins at 7pm.
This meeting will be held at our new location, the GateWay Conference Center, Building J, ciscoSystems. The address for this conference center is:
255 W. Tasman Drive
San Jose, CA 95134
Please enter through the front entrance of the building, and the conference center will be to your left. There will be signs.
For more information:
Rob Walker,
http://www.svlug.org/
 [gtk-list] Qt/KDE Netscape -- An estimate of Work!
[gtk-list] Qt/KDE Netscape -- An estimate of Work!1 Feb 1998
John McNulty wrote: I'm sure after Netscape's source code announcement, a number of people (like me) must have wondered about the possibility of a port to KDE and/or Qt. So I asked one of the Netscape engineers for an opinion on this. Below is the answer I got.
Depending on the number of people working on it, it could take anywhere between 2 months to an year. Of course, stripped down versions are possible in a shorter period of time.
- The GUI frontend is clearly seperated from the rest of the browser by a well defined API (which all 3 frontends - MFC, Mac, Motif - use).
- There are about 50 widgets ( ls *.c | wc -l) that are Netscape specific, which'll have to be ported.
- The GUI itself is composed of around 160 C++ files, which instantiate these widgets.
So if anyone put there is thinking about this, you can use this as a guideline to figure out how much work is involved.
--John
 ZINC Software
ZINC Software9 Feb 1998
Zinc's flagship product, Zinc Application Framework, is a very high- quality C++ GUI API and interface builder which supports popular desktop operating systems (Windows, Motif, DOS, ...) *and* which is scalable to embedded platforms as well (in 1/10th the space of Windows CE!).
Zinc has recently negotiated distribution agreements with popular Linux vendors to include ZAF with their CD-ROM distribution. Zinc has also been engaged by top embedded operating systems' vendors to provide reference ports of ZAF for their embedded OS.
For more information:
Robert Bishop,
Zinc Software Incorporated, http://www.zinc.com/
 EDA Software: Linux VHDL Simulator Sells Via Web
EDA Software: Linux VHDL Simulator Sells Via Web9 Feb 1998
Essex Junction, Vt. -- Despite considerable user interest, very few Linux-based EDA tools have become available. One of the first is a new Linux version of the Green Mountain Computing Systems VHDL compiler, available for $169 via the World Wide Web.
Green Mountain currently offers a DOS-based VHDL simulator, and Accolade Design Automation (Duvall, Wash.) sells a Windows-based version of the same simulator. The new version 2 of the Green Mountain VHDL compiler supports most, but not all, of the features of IEEE 1076-87 and 1993 VHDL.
The Linux version is a port of the DOS version and includes all the same features, except for the user interface. Both versions come with two simulation environments for batch or interactive simulation, precompiled IEEE packages, an online VHDL tutorial, a Motorola HC11 microcontroller example model and free technical support via e-mail.
Scott Thibault, president of Green Mountain Computing Systems, said he developed the Linux version because that freely distributed operating system is becoming more important in universities, which have made up Green Mountain's primary market. He said the Linux version is slightly slower than the DOS version because of its support for multitasking.
Linux has gained a following because it's viewed as a stable, robust operating system that gives PCs full Unix compatibility. Thus, commonly used Unix utilities such as "make" are available. Linux also has minimal memory requirements. The Green Mountain Linux VHDL compiler can run in about 8 Mbytes of RAM. The simulator can be ordered only by mail or over the Internet.
For more information:
http://together.net/~thibault
 EAGLE LINUX M68K
EAGLE LINUX M68Kfor AMIGA, Atari, Mac 68k and all computers based on the Motorola MC680x0 CPU is now available. The end user delivery starts the first week of March. Linux is pre-available on CDR for press and magazines.
Distribution:
Eagle Computer Products GmbH,
S.u.S.E. GmbH
Update CDs will follow every 2-3 months. Planned versionen which will come soon:
 Olicom Linux Token-Ring driver released
Olicom Linux Token-Ring driver released6 Feb 1998
Olicom is pleased to announce the release of a Linux Driver for Olicom's high performance Token-Ring Adapters OC-3118 and OC-3137. The driver is also compatible with the older OC-3136 adapter. The combination of Olicom's Token-Ring adapters and new Linux drivers provide superior performance in a Linux Token-Ring environment.
The driver has been tested with the (currently) latest version of the 2.0 kernel, 2.0.33. It will probably work with any 2.0 kernel, i.e. all of the kernels used by the Linux distributions, but this has not been tested and can not be guaranteed.
For the current development versions of Linux 2.1 the driver has been tested with version 2.1.78. Changes to the development kernel are occurring in rapid pace and compatibility can not be guaranteed.
The Olicom Linux driver is available from Olicom's WEB site http://www.olicom.dk/ (Europe) or http://www.olicom.com/ (US).
Pre-compiled kernels with the driver builtin - based on Linux 2.0.33 - for RedHat 4.2, RedHat 5.0 and other systems using the Linux 2.0.x kernel, are available from
ftp://ftp.olicom.dk/pub/releases/Unix-Driver/Linux/unsupported/
For more information:
http://www.olicom.dk/ (Europe)
http://www.olicom.com/ (US)
 GNU plotting utilities 2.0 released
GNU plotting utilities 2.0 released6 Feb 1998
Release 2.0 of the GNU plotting utilities is now available at ftp://ftp.gnu.org/pub/gnu/plotutils-2.0.tar.gz . It should soon be available via ftp from the GNU mirror sites. A list of mirror sites is appended below; please try them before you try ftp.gnu.org.
This is a major release. The centerpiece of the package is now `libplot', a function library for 2-D device-independent graphics. Libplot is installed as a DLL (dynamically linked library), on systems that support DLL's. Libplot now supports Hewlett-Packard Graphics Language (HP-GL and HP-GL/2) output, in addition to Postscript, xfig, Tektronix, and X11 output. So HP LaserJet and other PCL 5 printers are now supported.
The manual for the plotting utilities is now over 100 pages long. To install and print the documentation, be sure that you have the current release of the GNU texinfo package (v. 3.11) installed on your system. You may retrieve it from ftp://ftp.gnu.org/pub/gnu/texinfo-3.11.tar.gz .
For more information:
Mathematics Department, University of Arizona
Robert S. Maier,
 Data Plotting Library DISLIN 6.3c
Data Plotting Library DISLIN 6.3c6 Feb 1998
DISLIN is a high-level and easy to use plotting library for displaying data as curves, bar graphs, pie charts, 3D-colour plots, surfaces, contours and maps. Several output formats are supported such as X11, VGA, PostScript, CGM, HPGL, TIFF and Prescribe. The library contains about 400 plotting and parameter setting routines and is available for several C, Fortran 77 and Fortran 90 compilers.
Version 6.3c of DISLIN is now released for Linux. The supported compilers are GCC, G77, Imagine F, NAGf90, Absoft f77 and Absoft f90. Plotting extensions for the programming languages Perl 5.003 and Python 1.5 are included.
All DISLIN distributions for Linux are free. DISLIN is available from the DISLIN Home Page:
http://www.mpae.gwdg.de/dislin/dislin.html
and via FTP from the server:
ftp://ftp.gwdg.de/pub/grafik/dislin/
For more information:
Max-Planck-Institut fuer Aeronomie
Helmut Michels,
 ktalkd-0.4.1 - Enhanced talk daemon
ktalkd-0.4.1 - Enhanced talk daemon6 Feb 1998
ktalkd is an enhanced talk daemon with answering machine for Unix systems, designed to work under KDE, but can also work without it. It is available at:
ftp://aurora.resi.insa-lyon.fr/pub/people/dfaure/linux/ktalkd-0.4.1.tgz
ftp://ftp.kde.org/pub/kde/Incoming/ktalkd-0.4.1.tgz
Tested on Linux or BSD, with or without KDE.
For more information:
David Faure,
 angela! 1.7 BETA - graph editor w/ Tcl/Tk interface
angela! 1.7 BETA - graph editor w/ Tcl/Tk interface9 Feb 1998
angela! stands for:
A ngela is a
N atural
G raph
E ditor with
L ayout
A lgorithms
!
angela! is free of charge (GPL LICENSE)
It is intended to help the user creating simple graphs for courses, technical diagrams or simply demonstrating what graph algorithms can do.
The developpment platform is Linux 2.0.32 with glibc libraries as there are provided with RedHat 5.0. Porting angela! to other systems should not be difficult as it uses these Programs:
The actual version is at this time under the following URL:
http://www.mpi-sb.mpg.de/~pabst/angela/
For more information:
Oliver Pabst,
University of Saarland, Computing Center, Germany.
 Tsinvest, version 0.4, stock trading program released.
Tsinvest, version 0.4, stock trading program released.9 Feb 1998
The C sources to a stock trading program, tsinvest.tar.gz, version 0.4, are available at ftp://sunsite.unc.edu:/pub/Linux/Incoming/"> or ftp://sunsite.unc.edu:/pub/Linux/apps/financial/investment/. The sources are free for non-commercial use.
The program tsinvest is for quantitative financial analysis of equity values. An optimal portfolio investment strategy for multiple equities is computed. The program decides which of all available equities to invest in at any single time, by calculating the instantaneous future value of all equities, and using statistical estimation techniques to estimate the accuracy of the calculated values. Entropic techniques are used throughout. A tutorial is presented in the man(1) pages. A companion equity market simulation program is included.
For more information:
John Conover,
 Linux Logo 1.04 - shows system info with a linux logo
Linux Logo 1.04 - shows system info with a linux logo9 Feb 1998
linux_logo outputs a color ansi version of a penguin, accompanied by system info gathered from proc. SUPPORTS Linux, SMP, Atari m68k, and even some non-Linux OS's
USES [instructions included]:
Check out other programs at http://www.glue.umd.edu/~weave/vmwprod
For more information:
Vince Weaver, , http://www.glue.umd.edu/~weave/
 xfpovray v1.3 - An X interface for POV-Ray raytracer
xfpovray v1.3 - An X interface for POV-Ray raytracer16 Feb 1998
I would like to present a new version (1.3) of my xforms interface to the ray tracer POV-Ray. If you have ever used POV-Ray from the command line, you might find this program useful. Check:
http://cspar.uah.edu/~mallozzir/
Source code is available in tgz, bzip2, and rpm formats.
For more information:
Robert S. Mallozzi, http://cspar.uah.edu/~mallozzir/
University of Alabama
 Casio Digital Diary Backup/restore v2.2
Casio Digital Diary Backup/restore v2.217 Feb 1998
Casio Diary is a package that allows communication to the CASIO series of hand-held organizers based on a protocol posted by Knut Radloff, [email protected].
Version 2.2 has been tested on Linux2.x , Solaris2.x, sunos4.x. For both the BOSS and ILLUMINATOR models and is released under the GPL.
It is provided as is i.e. jamal is not to be responsible for any damages it causes to you, your CASIO or your environment.
Primary-site: http://sunsite.unc.edu/pub/Linux/apps/comm/
100kB casio22.tgz, 1kB casio.lsm Alternate-site: ftp://ftp.cyberus.ca/pub/users/hadi/casio/casio22.tgz
For more information:
Jamal Hadi Salim,
Ottawa, Canada
 Telnet98 - updated telnet source distribution
Telnet98 - updated telnet source distribution18 Feb 1998
Telnet98 is a new release of the ubiquitous "telnet" utility, based on the 1995 MIT telnet distribution from ftp.cray.com and net-dist.mit.edu. Telnet98 adds some new features to the distribution including new 'configure' based build and install scripts and support for additional authentication and encryption types.
Telnet98 can be downloaded from ftp://quasimodo.stanford.edu/pub/telnet/, and US/Canadian users can find instructions there for downloading source with strong (128-bit) encryption enabled.
For more information:
Thomas Wu,
Stanford University: Computer Science Department, CA USA
 Subject: fetchmail-4.3.7 - mail retriever for POP and IMAP
Subject: fetchmail-4.3.7 - mail retriever for POP and IMAP18 Feb 1998
The 4.3.7 release of fetchmail is now available at the usual locations, including http://earthspace.net/~esr/fetchmail/. Here are the release
For more information:
Eric S. Raymond,
Organization: Eric Conspiracy Secret Labs, http://earthspace.net/~esr
 leap 1.1.9 - A free RDBMS
leap 1.1.9 - A free RDBMS20 Feb 1998
LEAP is a free RDBMS (Relational Database Management System) that has been used as an educational tool in Universities around the world to aid students as they learn database theory. It allows relational algebra expressions to be entered directly into the system, and the results to be queried. It supports relational closure, so complete expressions can be deeply nested. Examples are included from popular database texts, including C.J.Date's "An introduction to database systems".
LEAP is entirely free (it is distributed under the terms of the GNU General Public License), and is very easy to install. All distributions contain the full 'C' source code. Versions exist for all Unix implementations, and Windoze 95/3.1/NT. Full documentation is included in the distribution, and is available on the web. LEAP is in active development (on a Linux 2.0 slackware system) by the author.
Full details, including links to the main ftp archives, are available on the LEAP web page:
http://www.dogbert.demon.co.uk/leap.html
http://www.brookes.ac.uk/~e0190404/leap.html
Strictly speaking LEAP 1.1.9 is BETA software, but extensive testing has shown no major problems.
For more information:
Richard Leyton,
 WMF - WebMailFolder 1.0.1 mail folder to html converter
WMF - WebMailFolder 1.0.1 mail folder to html converter20 Feb 1998
This tool is for converting mails to html and can be used for mailinglist archive.
It can be found on: ftp://sunsite.unc.edu/incoming/Linux/ or ftp://sunsite.unc.edu/pub/Linux/Incoming/ should be moved to ftp://sunsite.unc.edu/pub/Linux/apps/www/converters/
ftp://ftp.lugs.ch/incoming should be moved to ftp://ftp.lugs.ch/pub/linux/mail
For more details see the doc/ChangeLog or Norbert Kuemin, Swisscom,
http://www.lugs.ch/LUGS_Members/norbert.kuemin/wmf.html
 bash Book Released
bash Book Released27 Feb 1998
New Edition of the "Definitive Guide to bash" released--O'Reilly's Learning the bash Shell By Cameron Newham & Bill Rosenblatt now covers Version 2.0. This second edition covers all of the features of bash Version 2.0, while still applying to bash Version 1.x. New features include one-dimensional arrays, parameter expansion, and more pattern-matching operations. In addition, bash 2.0 is POSIX.2 conformant. This updated edition covers new commands, security improvements, additions to ReadLine, improved configuration and installation, and an additional programming aid, the bash shell debugger.
For more information:
O'Reilly & Associates, , http://www.oreilly.com/
 The Answer Guy
The Answer Guy 
 Can't Telnet to Red Hat 5.0 Server
Can't Telnet to Red Hat 5.0 ServerFrom: Brad Lackey,
I am trying to set up a LINUX web server for Colorado State = University - CIS Dept. I have Red Hat 5.0 Installed with user accounts = set up but I cannot telnet to the machine. I get the login prompt, but = none of the user accounts that I have created seem to work, including = root. they all give me "Login incorrect". I was wondering how to fix = this validation problem...
Thanks, Brad
 First I'll have to assume that you installed RH5 on a fresh x86 machine with no previous OS, and that you've just installed the package from a CD and have yet to apply any upgrades or patches to it.
First I'll have to assume that you installed RH5 on a fresh x86 machine with no previous OS, and that you've just installed the package from a CD and have yet to apply any upgrades or patches to it.
If that's the case -- fire up the old browser and go to Red Hat's "Errata" pages at:
http://www.redhat.com/support/docs/rhl/rh50-errata-general.html
There are about 30 upgrade packages there -- including fixes for the utils package (fixes 'vipw' command), and glibc (the core c libraries which most of your other programs depend upon through the magic of shared libraries).
I don't see a specific entry for the problem that you're describing -- and I haven't upgraded any systems to RH5 yet -- so I don't know if this problem is generic.
A quick search of Yahoo!/Alta Vista and DejaNews doesn't show a match to exactly this problem either -- but it does show that telnet to RH5 boxes is working for many people. (Many of the problems reported have to do with long delays, caused by the "double-reverse lookup" that TCP Wrappers uses to prevent most varieties of spoofing). So, given that the search string "+red +hat +5 +telnet +login" didn't give us an easy answer we'll have to do some troubleshooting.
Let's start with some questions:
Does your syslog (/var/log/messages or /var/log/security) tell you anything?
Have you run pw5conv to enable shadow passwords?
If you run 'vipw' ('vi' the /etc/passwd file) do the password hashes appear there?
Have you installed a different PAM (pluggable authentication modules) or modified its configuration (any of the files under /etc/pam.d/)?
I didn't see a new PAM RPM up at the site listed above -- though things like the initscripts package and the glibc package might help.
If these questions don't help you find the problem and resolve it I'd suggest that you grab a Red Hat 4.2 or a S.u.S.E., Debian or other distribution and install that. If you use Red Hat 4.2 you'll want to fetch all the upgrades for that -- and you might be able to install specific RH5 rpms (including the glibc which *should* co-exist cleanly with the libc 5.x that most (almost all) Linux distributions prior to RH5 rely on).
As a support volunteer I find Red Hat's decision to push the release of "Hurricane" out the door at the end of last year to be abominable. I suggested to them that they do a 4.5 first -- and wait until about March of this year for a 5.0 (hoping that glibc would be better understood, that PAM would move much closer to 1.0, and that the 2.2 kernel *might* ship by then).*
*** Please note: I don't have any "inside" hints as to when any of these event will occur. I don't know how long it will take to go from the 2.1.8x kernels through the inevitable 2.1.99.x flurry and get to 2.2. I read the kernel mailing list and cross my fingers like everyone else. Obviously Red Hat Inc (the company) and Caldera, and Yggdrasil, and many other organizations and individuals can help. If I were a programmer I might be able to help more.
However, I was sure that 5.0 was too soon -- and the 34 Mb of upgrades and patches that were available as of last November needed to be released on CD to save the 'net a bunch of bandwidth. (I occasionally cut these and similar new stuff onto CD's using my ISDN line and my CD-R and give them away. I'm hoping to give one or two away at tonight's SVLUG (Silicon Valley Linux User's Group) meeting where we'll be hearing from Bruce Perens of the Debian project, and Eris S. Raymond, whose paper on the "Crystal Cathedral" was cited as a key part of Netscape's decision to release their sources)).
I'd like to see Red Hat adopt a subscription model, where I can get monthly update of their "updates" and "contrib" mirrors for about $10/month. (I suppose it doesn't *have* to be Red Hat to do this, anyone with a CD-R and a reasonable trickle feed from the 'net could do it. Though the economies of scale don't work until we get a few hundred subscribers).
Heck, if there's enough interest I'll do it.
In any event, I hope one of these methods works.
At the risk of starting serious flame wars and raising questions about my "loyalty to the cause" (which cause we're not sure) I'd also suggest that you look at the OpenBSD (and FreeBSD and NetBSD) distributions if you don't have a specific reason for picking Linux for this application.
Linux is the most popular of the free Unix' -- but it's not the only one -- and it's not necessarily the best for all applications. OpenBSD, in particular, seems to be very well suited to multi-user "student use" and "computer lab" use. This is because Theo de Raadt and his team have found and corrected a large number of buffer overflows and other vulnerabilities in the sources for FreeBSD and NetBSD (and probably in the sources of many Linux utilities as well).
Obviously this depends quite a bit on your intended applications. However, if I was setting up a general use shell account system for a school lab, an ISP, or a USENIX "terminal room" I'd probably suggest OpenBSD.
For personal workstations I think Linux holds the edge in performance and applications availability.
--Jim
 Use the Source, Luke!
Use the Source, Luke!From: SuatChoo Lua,
Here there something that maybe you can answer me. From where i can get the information about Linux File system,memory managemant,and scheduling algorithm. Thank you!
coco
 In many ways I'm not the best person to answer this question. Remember that I am not a coder -- and I haven't contributed any programming to the Linux kernel (which I'm sure we all appreciate). However, I've read a bit of it -- and will offer some opinions.
In many ways I'm not the best person to answer this question. Remember that I am not a coder -- and I haven't contributed any programming to the Linux kernel (which I'm sure we all appreciate). However, I've read a bit of it -- and will offer some opinions.
If you want deep information about -- technical details -- about Linux filesystem, memory management, and scheduling internals than the obvious thing to do is to read the sources.
/usr/src/linux/kernel/sched.c is about 1700 lines long (about 80 pages). There are about 30 .c files under /usr/src/linux/fs (the filesystems directory) -- and about 160 .c files under that whole tree. Linux supports many different filesystems -- although the one that is considered to be "native" to Linux is the ext2fs.
A variant of this filesystem has been adopted by the FSF for their ongoing HURD project (which is a microkernel OS for which rms and the Free Software Foundation developed gcc, GNU emacs, and most of the applications and utilities that make Linux possible).
The code for ext2fs is about 5000 lines. Probably the simplest filesystem that ships with Linux is the Minix compatible one. Minix is a simple microkernel operating system written by Andrew S. Tanenbaum for inclusion with (and publication in) his text book on "Operating Systems: Design and Implmentation." That book is one of the seminal works on the topic -- and has probably been studied by every major contributor to Linux.
The memory management code is in /usr/src/linux/mm. It probably shows off the greatest innovations in the Linux kernel. The aggressive strategies here allow a Linux kernel to operate within a pretty modest footprint despite the "freeping creaturism" that some of its detractors lament.
Where to begin:
I hope you find all those interesting and informative.
--Jim
 'ifconfig' to Troubleshoot Dropped Ethernet Packets? Uh-Unhg!
'ifconfig' to Troubleshoot Dropped Ethernet Packets? Uh-Unhg!From: Chris Oliphant,
I have a HP Vectra XM2 4/100i computer with an onboard PCnet/32 ethernet chip running Red Hat Linux 4.0, kernal version 2.0.18. I currently am having problems communicating over the ethernet connection for the last three days. I want to use IFCONFIG to troubleshooting the problem, but don't understand how to use the command's output. My problems are excessive receive packets being dropped and excessive transmit errors. I am able to ping the onboard chip, and the port connect is good with other systems connected to it. But when I connect my Linux system to the port, I have problems. Please advise. Thanks for any assistance you may provide. --Chris Oliphant
 'ifconfig' is the "interface configuration" utility. It isn't a troubleshooting tool. I'd usually 'ping', 'tcpdump' and 'netcat'* or 'kermit'* for troubleshooting this sort of problem.
'ifconfig' is the "interface configuration" utility. It isn't a troubleshooting tool. I'd usually 'ping', 'tcpdump' and 'netcat'* or 'kermit'* for troubleshooting this sort of problem.
"for the last three days"? What happened then or before then? Did the link work fine before then? Did you upgrade your kernel? Change drivers? Add a new video card? Did this kernel/driver/module ever work acceptably with this ethernet card? With this system's mixture of other components? With a similar (so-called "identical") system?Excessive errors on an ethernet line suggests the following sorts of problems:
As an example if you put a few xterminals or diskless workstation on a network and they fetch all of their X resources, binaries and libraries over the wire (rather than tftp to a local RAM disk for example) then you can flood an unswitched ethernet segment in no time.
It is possible that some ether card on your segment is broken and "chattering" (generating spurious signals which corrupt the data frames (network layer "packets") from other cards. This is likely to show symptoms across the entire segment (all the machines will be affected). It is also possible that any particular card is damaged. It is also possible for the problem to be in a particular wire (are you using 10BaseT, coax/thin net, or (heaven forbid!) thicknet?), or even a particular port on one of your hubs (repeater, concentrator, whatever the "term du jour" for that thingie-me-bob is). It could be as simple as "someone kinked the wire by running it over with their chair wheel."
A good way to test for this is to get an ethernet "cross over" cable (sort of a "null modem" for 10BaseT) and plug it between the problem system and a known good one. This bypasses all the intervening components to help isolate the problem.
(Basic troubleshooting 101: identify all components, eliminate as many as possible for testing, continue simplifying the configuration -- and possibly the tests -- until something works, re-add components back until failure. That isolates the problem.)
Naturally you'll also want to try a 2.0.33 or 2.0.34 kernel to see if that helps.
--Jim
 Cthugha
CthughaFrom: kim angel,
Could you please tell me when Cthungha will be available for Win95? Thanks!
Kim Angel
 Sorry. Can't be much help there. I presume you mean Cthugha (no 'n') which would be the audio/video amusement (turn your $3K multi-media system into a $40 "discoteque" light).
Sorry. Can't be much help there. I presume you mean Cthugha (no 'n') which would be the audio/video amusement (turn your $3K multi-media system into a $40 "discoteque" light).
 Hmm....I detect a tad of dissatisfaction with the product!
Hmm....I detect a tad of dissatisfaction with the product!
 I've never run it. I have a lack of interest in the class of software. I had to look it up in the LSM (software map) to remember what it was -- since I mis-remembered it as a "game").
I've never run it. I have a lack of interest in the class of software. I had to look it up in the LSM (software map) to remember what it was -- since I mis-remembered it as a "game").
I have no idea if or when it would be available for Win '95 -- or even why anyone would port it. However, I'd contact the author/maintainer (should find his/her/their name(s) in the man pages or docs).
 What I am seeking is a program that is capable of applying digitized animation choreographed to audio sequences. Could you help me with this?
What I am seeking is a program that is capable of applying digitized animation choreographed to audio sequences. Could you help me with this?
 I'm the "Linux Answer Guy" (or, to be more specific and a little less pretentious, the "Linux Gazette Answer Guy").
I'm the "Linux Answer Guy" (or, to be more specific and a little less pretentious, the "Linux Gazette Answer Guy").
It appears that Cthugha *is* just what you want -- for Linux. I'm not the "Windows '95 Answer Guy." A role which I probably would be wholly inadequate at since I don't run it on any of my systems and I don't like what little of it I've had to run.
Despite this I can offer you a pretty simple piece of advice:
Ask the author.Another possibility is that you could try the port yourself. I'm not sure what the licensing of Cthugha and its sources is -- but it's probably GPL. That license lets you port it to any OS or platform you like -- or pay anyone else to perform the port to your specs.
If you should find that the port to native Windows API's is too difficult you could try DESQview/X (which offers X Windows API's over DOS) or you could try OpenNT (from Softway Systems at www.softway.com). OpenNT offers reasonably complete Unix API's -- and some X Windows if I heard correctly -- and runs under NT. I have also heard of several developers tools that purport to compile Unix/X Windows code into native MS Windows API's. However I don't have any experience with them, nor any personal interest in them.
-- Jim
 xdm Login doesn't!
xdm Login doesn't!From: Cesar Augusto Kant Grossmann,
I run my Linux Box in the "graphics mode" (changing inittab accordling) = bu I can't login as normal user. When I try to login as normal user, the = screen flickers like a logout in the X, and the login screen comes back.
 This is also referred to as "using 'xdm'" (X Display Manager) which provides a GUI login to X.
This is also referred to as "using 'xdm'" (X Display Manager) which provides a GUI login to X.
You don't mention what sort of system you have (which distribution what architecture/platform, what packages you've installed or updated, etc). You also don't mention whether you can login via a text mode console (VC/VT) or via telnet or a serial line.
If you can, the problem is likely to be a mismatch between your 'xdm' binary and the authentication model/settings that you have for your other 'login' modes.
This is one area where the FreeBSD crowd definitely had a better model. Under Linux you can use the old-fashioned (traditional -- and insecure) authentication mode where the hashes of your passwords are stored in the /etc/passwd. Alternatively you can install or enable some variation of the "shadow" suite. This removes the password hashes from the /etc/passwd file and stores them in a different file -- one which is only accessible to privileged (SUID) programs -- and not readable by normal users.
The purpose of all that is to make the system more resistant to dictionary and cryptanalytic (brute force or otherwise) attacks. In other words using the 'shadow' options is more secure than allowing normal users to just snarf the hashes up, and copy them to a machine running 'crack'.
The problem is that there are many programs that authenticate users under Unix/Linux. In addition to login there's xdm, ftpd, xlock, vlock, screen's lock feature, popd, imapd, the passwd command etc. In FreeBSD they modified the libraries -- and ensured that all the programs were linked against the same shared library. This hides the details -- because the library calls that "getpwent()" (get password file entries) automatigically merge the passwd hash from the shadow file (called /etc/pwdb.master? or somethine like that -- in FreeBSD) if that file exists and is readable.
Thus unprivileged files on a shadow enabled get pw entries with an "obscured" password field (usually just a "x") while privileged (SUID) program get a merged one that's suitable for comparison to a properly crypted/hashed password as provided by an alleged user.
The other advantage to the FreeBSD method is that changing the hashing algorithm (from the traditional 56-bit DES on a string of zeros -- to a MD5 sum) is relatively easy -- only has to be supported in one place (the shared libraries) and doesn't require that all the other programs be changed. (Another feature of the FreeBSD password/account management libraries is that they support dbm hashes of the account names -- meaning that *huge* lists of accounts are possible without suffering a "linear" increase in login/authentication response times)
For now Linux has three different, and partially incompatible account/authentication schemes:
Although Red Hat has shipped their last 2 or three releases with PAM -- it isn't quite all there yet. The most recent version of PAM is about 0.63 (beta). However -- if you installed a recent Red Hat Linux (4.2 or 5.0 with patches) you should be able to use its xdm and all of their stock utils without trouble.
If you compiled your own 'xdm' or fetched it from somewhere you should consider recompiling it -- but looking for options that relate to "shadow" support.
 What seems to happen? Where I can find more informations about these? A FAQ or something like...
What seems to happen? Where I can find more informations about these? A FAQ or something like...
 I'd start by reading the Shadow HOWTO. I'd also suggest a web search on PAM (pluggable authentication modules): Here's some URL's I have for them:
I'd start by reading the Shadow HOWTO. I'd also suggest a web search on PAM (pluggable authentication modules): Here's some URL's I have for them:
 Sorry for my bad English, but I think it's better than your Portuguese...
Sorry for my bad English, but I think it's better than your Portuguese...
 Undoubtedly your English is better than my Portugese -- or even my French (I've never studied the former and only had a couple of high school years of the latter). --Jim
Undoubtedly your English is better than my Portugese -- or even my French (I've never studied the former and only had a couple of high school years of the latter). --Jim

Here's this month's account of the triumphs, trials and tribulations that I caused myself or encountered since the last time, and a couple tips that may come in handy and increase your understanding of linux.
Like I said, I'm not familiar with all of screen's features, but to use it, basically you type:
screen progname
and your screen session is started in VT0. To add more VTs you can use:
Ctrl-a c
and to change from one screen to another:
Ctrl-a 0-9
and you can change from screen to screen, depending on how many you have opened. Note that the screens are numbered 0-9 rather than 1-10, the only clumsy feature of this program, IMHO.
tabit will complete the filename so you can get on with your life and file manipulation.Play with this feature, if you haven't typed enough of the name to be unique, it will sit and stare at you, try another character or two.Likewise, if you specified the wrong directory,you'll get nada.
..and its close relative
.The details for a quick cd areas follows: as you may be already aware, the dots represent your current directory(single dot) and parent directory (double dot).By CDing to
..you will be magically transported to the parent directory, ie from /usr/bin to /usr.You can use:
cd -to return to the previous directory, and to go up two or more levels:
../../and so onwill work. The single dot is not as useful in terms of cd, but it does have its use. If you are in a directory that's not in your path, or dont have
.in your path statement, you must give a path to run an executable file. This is easily accomplished by typing:
./execunamewhich will give the relative pathname, allowing it to be found and run. There are a few good reasons why using the single dot in your path statement isn't a good idea, suffice to say, if you'd like more info on that subject, you should read up on system security.
ls -aFwhen you actually meant to type
diror
cpwhen what you wanted was
copyyou can create batch files(like shell scripts) named for your favorite unix commands, using your favorite switches. Not as cool as dosemu or just plain staying in Linux, but ya gotta do what ya gotta do.
If you have a subject that you would like to see covered or have any corrections, comments or flames let me know, and I'll look into the matter.
See you next month!
This column is devoted to making the best use of Emacs, text editor extraordinaire. Each issue I plan to present an Emacs extension which can improve your productivity, make the sun shine more brightly and the grass greener.
You've probably heard the hype about ``Internet-ready'' operating systems where you can access the Internet with a click of your mouse. Well, users of the customizable Emacs user interface have had the Net only a keypress away since as early as 1989!
Emacs has built-in networking capability, which it uses for connecting to news or SMTP servers and for web browsing. To illustrate its use, here is a bit of code which opens a TCP connection to port 13 of your local machine to request the current time :
;; usage: M-x display-date
(defun display-date ()
(interactive)
(let ((stream (open-network-stream "DAYTIME" nil "localhost" "daytime")))
(set-process-filter stream 'my-process-filter))
(defun my-process-filter (proc string)
(message "Current date is %s" (substring string 0 -1)))
This code --which assumes you're running inetd-- should display something like the format of date in the minibuffer. The rich set of primitives and the integrated error management provided by Emacs make it easy to program useful utilities; consider how many lines of code would have been required to provide the equivalent functionality in C.
Ange-ftp is a package by Andy Norman which allows Emacs to see the entire Internet as a virtual filesystem. It adds remote editing capability by mapping requests for remote files to FTP commands. For example, if you ask Emacs to open a file named
/[email protected]:~/.emacs
then ange-ftp will spawn an FTP process, connect to the host salines.cict.fr as user marsden, CWD to my home directory, GET my Emacs initialization file and display the file as if it were on your local filesystem. If ange-ftp needs a password it will read one from the minibuffer. If you make changes to the file and save it, it will be PUT back to the server for you. You can even copy files from one remote machine to another by typing M-x copy-file RET /user1@host1:/path/to/file1 RET /user2@host2:/path/file2 ; ange-ftp looks after opening two ftp connections for you.
Ange-ftp comes pre-installed with Emacs (XEmacs features efs, a complete rewrite by the same author). The only customization you might need to make is to configure a gateway, if you don't have direct Internet access. You can use ~/.netrc to configure default logins for oft used hosts in the traditional way (and even passwords if you're foolhardy).
Perhaps the most elegant feature of ange-ftp is its seamless integration with Emacs; the only visible change it introduces is the extended filename syntax. Filename completion (by pressing TAB in the minibuffer) is available on remote hosts in the same way as on your local machine. Ange-ftp works well with Dired, the directory editor, allowing you to browse though distant machines, operate on several remote files at once, etc. It also works with bookmarks, so you can memorize an interesting spot on your favorite ftp server, and jump back to the same spot next week with ease. Take a typical usage: ask Emacs to open the following directory (with C-x C-f or from the Files menubar) :
/[email protected]:/pub/linux/kernel/
You will be presented with a directory listing many different releases of Linux kernels (if you have a line like default login anonymous password user@site in ~/.netrc then ange-ftp can infer the anonymous@ for you automatically). Type C-x r m to bookmark the location. There's more on bookmarks in Jesper Pedersen's article in issue 7 of the Linux Gazette.
Emacs-w3 (also referred to by some as Gnuscape) is a web browser written by William Perry in Emacs Lisp. It is fairly sophisticated in certain respects, having been the first production browser to support cascading style sheets. It understands tables, and can display images inline under XEmacs, or by invoking external viewers when hosted by GNU Emacs. Its author notes that Emacs-w3 is yet another reason never to leave the comfort of the One True Editor, but to me it serves more as a reminder of the deficiencies of Emacs Lisp : it is slow, and has a tendency to block while waiting on a slow link (unfortunately Emacs is not multi-threaded, though you can set the variable url-be-asynchronous to t to reduce this annoyance). If you want to try it out get the latest version from the betas directory, which has many improvements over the version distributed on most Linux CDROMs.
browse-url is an nifty Emacs extension which can dispatch references to URLs to Mozilla or to Emacs-w3. It does this by using Netscape's remote invocation protocol, which as a side note even works when you're running the browser on a distant machine (the implementation uses the X11 inter-application communication protocol). Emacs features its own remote control mechanism which lets you send commands to a running Emacs (even on another machine), called gnuserv/emacsclient, which I might talk about another time.
Recent versions of Emacs are set up to use browse-url in mail and news reading modes. URLs should be highlighted when you pass the mouse over them, and you can click on them with the middle mouse button to invoke your favorite browser. Here's how you can set up browse-url to use Mozilla when you're running X11 and Emacs-w3 otherwise :
(if (eq window-system 'x)
(setq browse-url-browser-function 'browse-url-netscape
browse-url-new-window-p t)
(setq browse-url-browser-function 'browse-url-w3))
Another more indirect use of browse-url is WebJump by Neil W. Van Dyke. This Emacs plugin provides a programmable hotlist of interesting web sites with which to feed your browser. Perhaps its most interesting feature is the ability to send a query to Internet search engines such as AltaVista and Yahoo! without having to load the first page of ads, but it also includes features for dispatching searches to FAQ and RFC archives, to the online Webster or Thesaurus, or to bring up an appropriate page of the Java API. Naturally (this is Emacs) you can extend it to include your own favorite sites. You might find yourself using it more than your browser's bookmarks.
ffap is a powerful package which extends the find-file command (the one which prompts for a file name in the minibuffer, normally bound to C-x C-f). It searches the text around the cursor position for something which might represent a filename -- a file in the current directory, a C #included file, a newsgroup reference, an ange-ftp style reference to a file on a remote machine or an URL -- and prompts you either to open that file, or to send the URL to a browser (via browse-url). Once experiencing this you quickly get sick of typing filenames into the minibuffer, and may find yourself inserting ``hyperlinks'' in strategic places in your files to save typing. ffap is distributed with both Emacs and XEmacs; I bind it to the F3 key as follows :
(autoload 'find-file-at-point "ffap" nil t)
(define-key global-map [(f3)] 'find-file-at-point)
or if you prefer you can simply override the traditional find-file by saying
(autoload 'find-file-at-point "ffap" nil t)
(define-key global-map [(control x) (control f)] 'find-file-at-point)
ffap is pretty good at determining interesting filenames; it even knows how to recognize RFC names, and from which server they may be obtained. It goes to the trouble of pinging remote machines to determine whether they are alive, and can naturally be extended to recognize personal types of filename references. To conclude on filename shortcuts, you might enjoy Noah Friedman's fff (Fast File Finder) which helps you find files hidden somewhere deep in inode-space by querying your locate database (part of the GNU findutils).
Several people wrote to me with comments on last month's article on jka-compr. told me he prefers crypt++, which provides on-the-fly decryption and encryption as well as automatic compression and decompression. Whereas jka-compr trusts the filename extension, crypt++ reads the first few bytes of the file to determine its type. The package also has functions for dealing with DOS-style linefeeds which you might find useful if you have to exchange files with other operating systems, although you could just as well say (standard-display-ascii 13 ""), which simply hides those ^M characters. Crypt++ is not a standard part of Emacs (it's not included in the GNU Emacs distribution, though it is bundled with XEmacs). I haven't tested its cryptographic capabilities, because
<POLITICS>
As a French citizen I am prohibited from using any form of encryption. In France encryption requires authorization from the President, which is accorded only to large military companies and to financial institutions (and then only if the keys are held in escrow). These laws are one of the reasons holding back the incorporation of kernel-level support for encryption in Linux. Before accusing France of being backward, please consider the fact that countries such as Iran, China and Russia impose similar restrictions on the freedom of their citizens.
</POLITICS>
If you're using the latest version of XEmacs (20.3 stable as of this writing), the suggestion I make last month for enabling jka-compr won't work. The XEmacs maintainers have decided that the behaviour of your editor shouldn't be modified by loading an extension module, but by calling an appropriate initialization function. The correct way of enabling jka-compr is to say (toggle-auto-compression 1 t). Sorry 'bout that, folks.
In the next issue I'll review ediff, a powerful interface to diff and patch. Don't hesitate to contact me at <[email protected]> with comments, corrections or suggestions (what's your favorite couldn't-do-without Emacs extension package?). C-u 1000 M-x hail-emacs !
PS : Emacs isn't in any way limited to Linux, since implementations exist for many other operating systems. However, as one of the leading bits of open-source software, one of the most powerful, complex and customizable, I feel it has its place in the Linux Gazette.
 |
|
 |
muse:
|
In this months column I'll be covering the following:
 |
XFPovray 1.3announces a new version (1.3) of his XForms interface to the ray tracer POV-Ray. If you have ever used POV-Ray from the command line, you might find this program useful. Checkhttp://cspar.uah.edu/~mallozzir/ Source code is available in tgz, bzip2, and rpm formats. Robert S. Mallozzi |
XMRM 2.0 (Alpha release)The Institute of Computer Graphics at Vienna University of Technology, Austria, announce the release of XMRM 2.0alphaXMRM (multi resolution morphing for X) is an image morphing program written for XWindows. A special feature of this program, which is not found in other morphing packages, is the ability to control the morphing speed of details in relation to the morphing speed of big features. Check out the XMRM homepage: For a few animated GIFs visit the Online manual: For download got to: Greetings, The XMRM-Team <> |
||
FREETYPE 1.0 The FREE TrueType Font EngineCopyright (C) 1996-1998 The FreeType Development TeamThe FreeType engine is a free and portable TrueType font rendering engine, available in ANSI C and Pascal source code. It has been developed to provide TrueType support to a great variety of platforms and environments. It's a clean-room implementation that is not derived from the original TrueType engine developed by Apple and Microsoft, though it matches it regarding rendering quality. To our knowledge, it's the only royalty-free complete TrueType engine available. For more information, please visit the Freetype web site at: |
Thats its. Not much in the way of announcments this month. I had a few more, but lost them pasting them into my XPostitPlus program. Thats the first time its crashed in that manner - where I lost the data. Bummer. | ||
A: Ron Parker responded on the IRTC-L discussion list: Whenever POV-Ray detects a sufficient change, the threshold, in colour from one pixel to it's neighbour, it will calculate the in-between color pixels by shooting multiple rays into the scene, rather than just one, to determine the colour. The higher the "+A" number is (from 0 to 1), the more rays will be shot into the scene, and the smaller a difference in colour from one pixel to the next will be needed to cause the anti-aliasing to be brought into effect. Anti-aliasing is triggered when the threshold between two pixels is reached. The number of rays is controlled by +R, and the "spread" is controlled by +J. Setting +A0.1 will trigger on smaller color differences than +A0.3, so it actually anti-aliases more than higher values of +A. All this is the description for +AM=1. Adaptive supersampling (+AM=2) works somewhat differently.
For more information, see section 6.2.5.4 of the POV documentation.
Ron Parker * * http://www2.fwi.com/~parkerr
Q: I took an image to a printer today who requested that I bring back the image when I have increased the resolution from 72 pixels/inch to 300 pixels /inch. I cant locate how to do this with the GIMP. Any pointers?
A: You can scale the image, but that will decrease the quality of the image. The best way to deal with images you plan to print is to plan to create them using the correct resolution. For example, if you want an 8.5" by 11" image at 300pixels/inch:
These scripts were created using Perl 5.004, Linux 2.0.32, and POVRay 3.0. I'd be honored if you would like to include a link from your excellent graphics site to my page at http://www.frozenwave.com/~hixson/projects.html.
, Senior Software Engineer @ NetManage, Inc., writes:
writes:
writes to the GIMP User mailing list:
and you're all set. If you have more than one device connected to the scsi bus (re: cable) then you'll need to figure out which one of the /dev/sg[x] devices maps to your scanner. Then link that one to /dev/scanner.
also wrote to the GIMP User mailing list:
The scanner I chose from the list of scanners I reviewed last year for my Graphics Muse column in the Linux Gazette. I first tried a 610s, but it only worked in greyscale modes. So I exchanged it for the more expensive (about $250) 1200s. Works quite well with the Umax drivers. Image quality is excellent. I've been scanning hardware (twisted pair and thinnet cables), and my hand once, and the scans were quite good although very dark. I just brightened them up with xv and the GIMP and all was well.
However, I haven't tried the scanner and drivers in conjunction with SANE.
Marco Iannacone wrote:
What he might be talking about is the use of tiles, which may appear to update slowly, wherease in Photoshop they may all appear almost at once (I've never used Photoshop, so I don't know if this is true or not). So before I can answer "is GIMP slower than Photoshop" I need to know by what means you've been measuring the two.
wrote:
writes:

Adding an text links is fairly easy to do and updating them simply requires editing the HTML. But text links lack pizazz. Images used as text links are better, but aside from using JavaScript to do image rollovers, the images are fairly static. They lack the feel of a real user interface. Image maps are no better and, in fact, don't even allow rollover changes as easily making them even more static than individual images used as links.
Fortunately, issues such as this is part of why Java exists. Java allows for more programmatic interfaces. These interfaces can take on the more familiar menu-based interfaces that readers will be accustomed to. Although it can be argued that such interfaces are not any better than static image maps, for the sake of this article we'll assume that menuing systems are a good thing.
XeoMenu is a simple Java program from Patrick Chan at Xeo (www.xeo.com) that overlays a menuing system over an image in a Web page. The program is run as an applet and is used by embedding it within HTML source code. Readers can retrieve a copy from http://java.sun.com:81/share/classes/menu/source/source.html. Java source code is included, along with an example HTML file, sample images, a users manual (a sort of man page in HTML) and the compiled Java byte code. There is also a second version of the code, called horizMenu, that permits menus to be layed out horizontally instead of vertically. Since I can't seem to get Java working on my Red Hat 4.2 system (neither through the javac compiler nor through my version of Vibe - something about my CLASSPATH is not set up right I think), I won't be able to provide information on compiling the source in this article. If I do get javac and/or Vibe working, I'll start talking about how to compile Java programs. If anyone has a write up of what I need to do to get my stock RH 4.2 version of the Java compilers working, please drop me a line.
To use XeoMenu you need to first create an image that contains two parts: The menu as it is displayed without the mouse over the image and the image as it would look if the mouse were over different parts of the original. For our example, we'll use the following image:
 The image is divided into 2 halves. The left half is the image as it displays without the mouse over it. The image is actually going to be subdivided into a top (Linux) and bottom (Gazette) section. The right side, then, shows how each section will be displayed when the mouse is over that section. For example, if the mouse is over the word Linux in the image then the blue Linux text will be displayed. By default, the red colors (the left half of the image) is displayed.
The image is divided into 2 halves. The left half is the image as it displays without the mouse over it. The image is actually going to be subdivided into a top (Linux) and bottom (Gazette) section. The right side, then, shows how each section will be displayed when the mouse is over that section. For example, if the mouse is over the word Linux in the image then the blue Linux text will be displayed. By default, the red colors (the left half of the image) is displayed.
Now, in order not to annoy readers without Java support, you need to move to the next section of this article, which will show how the Java application is used and what it looks like when it runs. You will need a Java compatible browser to view this part of the article.
 |
X Server UpdateI've been doing this column now for over a year and writing for Linux Journal on and off for another year. In that time I haven't really addressed one of the more obvious topics related to doing graphics on Linux - the X server. Part of the reason for that is that I don't have the resources to test a bunch of different server configurations. If I got paid to do this it would be a different story, but this column is born from whatever time and system resources I can spare each month.Still, I get requests fairly often asking for information about what 3D video cards are supported under Linux and which ones support various hardware extensions such as the X Input Extension. Most of the questions specifically ask "which are supported under XFree86". But some readers ask about support in general, either free or commercial. Well, I thought it was time I sent a query to the various vendors and find out where things stand. The email I sent was fairly generic. It read as follows: This query was sent out around the 12th of this month to Xi Graphics, Metro Link, SuSE, and the XFree86 project. I received responses from all 4, however Metro Link did not receive my query immediately and so their response came in too late for this article. I will cover Metro Link's response next month. Please note that this article is intended to list which servers support what features/devices and is not intended to explain how to use those features. The responses have been edited to remove what appeared to be editorial comments, where recognizable. I will refrain from editorializing on these responses in this article as well. The first reply was nearly immediate and came from at SuSE. He sent two emails, one as the Vice President of The XFree86 Project, Inc. and one as the Lead Developer, S.u.S.E. GmbH. Dirk wears both hats, and therefore his comments are considered official responses, one from each organization. Both responses were direct and to the point. First his XFree86 response:
The other replies came from Xi Graphics. Both Thomas Roell, President of Xi Graphics and technical architect for their servers, and Jeremy Chatfield responded. Thomas wrote:
Jeremy Chatfield followed up with the following (edited partially for length):
|
|
 |
|
Linux Graphics mini-Howto Unix Graphics Utilities Linux Multimedia Page Some of the Mailing Lists and Newsgroups I keep an eye on and where I get much of the information in this column: The Gimp User and Gimp Developer Mailing Lists. |
 |
More...
|
| © 1998 |
 |
Looking through my backlog of things to do for the Muse, I decided to take a look at VRWave. At a minimum I wanted to see if I could simply get it to run. Hopefully, I would be able to say something intelligent about the source code and build environment as well. I jumped on the Internet and went off to grab a copy of the package from a US mirror of the VRWave Home Page (http://www.iicm.edu/vrwave). The first thing I noticed was that there were both source and binary distributions available. The binary distributions cover a few flavors of Unix, including ports for Linux 2.0. There are actually two versions of the binary distribution - a Java 1.1.3 based version and a Mesa version which uses Java 1.0.2. These are actually the platform specific libraries needed by VRWave. I grabbed both along with the gzipped Common tar file which must accompany any binary version that is downloaded. The Mesa version is not compiled with any of the hardware accelerated drivers available for Mesa. If you want to use those drivers you need to recompile the source with the Mesa package properly built with the drivers of interest. Also, the Mesa code is statically linked into the platform specific libraries, so you shouldn't need any other libraries or files outside of those contained in the Common tar file and the platform specific tar file.
The directions say to unpack the Common file first, then cd into the vrwave-0.9 directory this process creates and unpack the platform specific files. The first time I did this I didn't do it in the right order and got myself confused. So I redid the unpacking, following the directions. Its true - men never read the directions. The instructructions in the INSTALLATION file for running VRWave are quite complete so I won't rehash them here. Just be sure you actually read the file! In my environment I use Java 1.0.2, the default installation of Java on Red Hat 4.2, so I set my CPU environment variable to LINUX_ELF. You may need to set it to LINUX_J113 if you have the Java 1.1.3 package installed on your system.
Once you set up a couple of environment variables you're ready to start vrwave. Since VRWave uses your Java runtime environment, be sure your CLASSPATH is set correctly first. On my Red Hat 4.2 system I have it set as follows:
java.lang.InternalError: unsupported screen depth
VRwave: could not load icons at /home/mjhammel/src/graphics/vrwave2/vrwave-0.9/icons.gif
VRwave: could not load logo at /home/mjhammel/src/graphics/vrwave2/vrwave-0.9/logo.gif
java.lang.InternalError: unsupported screen depth
at sun.awt.image.ImageRepresentation.setPixels(ImageRepresentation.java:170)
at sun.awt.image.InputStreamImageSource.setPixels(InputStreamImageSource.java:459)
at sun.awt.image.GifImageDecoder.sendPixels(GifImageDecoder.java:243)
at sun.awt.image.GifImageDecoder.readImage(GifImageDecoder.java:295)
at sun.awt.image.GifImageDecoder.produceImage(GifImageDecoder.java:155)
at sun.awt.image.InputStreamImageSource.doFetch(InputStreamImageSource.java:215)
at sun.awt.image.ImageFetcher.run(ImageFetcher.java:98)
at sun.awt.image.ImageRepresentation.setPixels(ImageRepresentation.java:170)
at sun.awt.image.InputStreamImageSource.setPixels(InputStreamImageSource.java:459)
at sun.awt.image.GifImageDecoder.sendPixels(GifImageDecoder.java:243)
at sun.awt.image.GifImageDecoder.readImage(GifImageDecoder.java:295)
at sun.awt.image.GifImageDecoder.produceImage(GifImageDecoder.java:155)
at sun.awt.image.InputStreamImageSource.doFetch(InputStreamImageSource.java:215)
at sun.awt.image.ImageFetcher.run(ImageFetcher.java:98)
These may be due to either an incorrect Java configuration on my system or because the Java 1.0.2 libraries do not support the TrueColor (24 bit depth) visual I'm running with my X server. In either case it didn't seem to matter, as the window opened and I was able to begin playing with VRWave. Also, during all my experimentation I had no display or color problems at all.
The first thing I should say at this point is that I know very little about VRML other than its a language for describing navigable 3D worlds. VRML 2.0 includes features such as spatial sound, where the sound of an object in the distance can grow louder as the object is moved closer. To my knowledge VRWave does not yet support sounds, but I didn't test any VRML worlds in which sound was availalble. In any case, what I'll describe here is what an casual user might encounter, what someone who is just beginning to explore VRML might find interesting and useful. Also please note that the slight blur in the images is due to reducing them from the screen captures in order to fit the image in a 640 pixel wide Web browser.

The image above show the initial window if no input file is provided on the command line. You can specify any VRML file as an input file. These carry the .wrl extension in the file name and you can find numerous example in the examples directory in the distribution. Scene files are ordinary text files, not unlike the POV-Ray programming language in a sense. The look like the sample code below, which is the code for the convexify.wrl example:
# sample for applying perface materials onto non-convex shape
# kwagen/mpichler
Viewpoint
{
position 5 5.25 10
orientation -0.6 0.8 0.1 0.5
}
Shape
{
geometry IndexedFaceSet
{
coord Coordinate
{
point [ 0 0 1, 1 0 1, 3 4 1, 2 4 1, 1 2 1, 1 4 1, 0 4 1,
0 0 0, 1 0 0, 3 4 0, 2 4 0, 1 2 0, 1 4 0, 0 4 0 ]
}
coordIndex
[
0 1 2 3 4 5 6 -1 # front, lt. green
0 7 8 1 -1 # red
1 8 9 2 -1 # blue
2 9 10 3 -1 # yellow
3 10 11 4 -1 # cyan
4 11 12 5 -1 # magenta
5 12 13 6 -1 # dk. cyan
6 13 7 0 -1 # dk. magenta
13 12 11 10 9 8 7 # back, dk. green
]
color Color { color [ 0 1 0, 1 0 0, 0 0 1, 1 1 0, 0 1 1, 1 0 1, 0 0.5 0.5, 0.5 0 0.5, 0 0.5 0 ] }
# colorIndex [ 8 7 6 5 4 3 2 1 0 ] # reverse color binding
colorPerVertex FALSE
convex FALSE
}
}
The following table summarizes most of the features in the VRWave main window:
| Window Feature | Description |
| File | Basic file input/output functions, plus camera information. |
| Navigate | Set mode for movement through VRML world; reset and align functions for current view. |
| Display | Lighting, rendering (static and interative) methods, colors, background, transparency, etc. |
| Help | HTML based help system that relies on Netscape. Netscape must be in your path for this to function properly. |
| Flip | Navigation mode; Scene translation around origin and zoom. |
| Walk | Navigation mode; move forward, backwards, sideways pan and move "eyes". |
| Fly To | Navigation mode; sets a Point of Interest from which all other movements in this mode are relative. |
| Heads Up | Places a "heads up display" in the center of the viewing area; 3 navigation types in display: eyes, body and pan. These correspond to the same types of movements that Walk provides but gives visual cues to movement settings. |
| Behaviour | Purpose unknown |
| Interaction | Purpose unknown |
An example of movement through this scene would be to hold down the middle mouse button (with the Flip button pressed as it is in the example image below) and drag it around the viewing area. This would rotate the entire room and its contents around the origin, which is positioned, but not visible, in the middle of the viewing area. When this movement is started the image will change to a wireframe view to speed processing. The use of wireframe, flat shaded, smooth shaded and textured objects during navigation and static display (when you aren't moving the scene around) can be controlled from the Display option in the menu bar.

This scene is probably the nicest image, asthetically speaking, of all the examples. The image fills the viewable area and is a complete room. If you navigate around the room you quickly learn that the walls to the room disappear if you're viewing area would be blocked by those walls For example, tilt the room down, then rotate it to the left. You're view of the room is now outside of the right wall, but in order to view the inside of the room the right wall is not drawn. You can change this behaviour by using the Display->Two-sided Polygons option and setting this option "On". The default setting, Auto, will not display the wall if it gets in your way. Turning this option on causes the back sides of the walls to become visible, and so your view inside the room is blocked.

In this next example the Heads Up option is selected and you can see the three view functions displayed in the middle of the viewing area. These small boxes don't move with the rest of the scene as you drag it around the viewing window. They stay centered in that window. A red line is drawn from the center of one of these boxes to the current cursor location showing direction and speed (longer lines give faster speed).
The movement of the small sphere in this image is managed through the use of the left mouse button, but only when the cursor is over the large green box. Moving the cursor, left mouse button held down, moves the sphere around the viewing area. If the mouse leaves the area of the box then the sphere stops moving. Note that the area of the box does not mean just a side of the box - it means what ever region of the box is actually visible to the user.
If you have a fast enough computer and enough memory you can turn on interactive texturing. This allows you to view the the objects in the scene with their full textures displayed while you move the scenes and objects around the viewing area. Although I can't show this feature here, I can show you another example scene which has a texture map applied to the sides of a cube. The first example shows the texturing on a cube with Two-sided Polygons turned off. The next example, which is a full sized capture so you can see the details a little better, shows the same image with Two-sided Polygons turned on.


The README file that comes with the binary distribution states that an online users guide for VRWeb (VRWave's predecessor) is available from http://www.iicm.edu/vrweb/help. However, this link doesn't seem to work any more. I browsed the main VRWave web site and found a link to http://www.iicm.edu/vrwave/release, which contains various online documentation. Unfortunately, I didn't find a users guide per se. The best printed help available will be the help/install.html and help/mouse.html files in the runtime directories from the binary distribution. In particular, the mouse.html file contains detailed information about mouse and keyboard bindings for scene navigation.
If you are just getting started with VRML and would just like to look at a few examples, this is a good place to start. You will need to have a working Java environment - one that can run Java applets if not compile Java code. Other than that, installation is a breeze and there are enough example files to keep you at least midly entertained until you can write your own VRML worlds.
 |
| © 1998 by |
More...
|
| © 1998 |
 |
This first example shows the basic workings of XeoMenu. Note that when you place the mouse over either word in the image it changes colors and shifts slightly in position. The latter was originally just a typo but I liked it the effect so much I left it in. The "Linux" text also provides a drop down menu when you place your cursor over it. The menu contains two simple entries. Moving the mouse over either entry would take you to another page (although the links in this source are fictitious - they don't really exist).
The applet code for this first example looks like this:
<PARAM NAME=menu0
VALUE="0 0 150 100|151 0 150 100|0 0|d|/path/to/file-1.html|What is Linux?|/path/to/file-2.html|How can I get it?|/path/to/file-3.html">
<PARAM NAME=menu1
VALUE="0 101 150 100|151 101 150 100|0 101|d|/nav/new/index.html">
</APPLET>
The next two lines give the copyright and program author, giving credit to Sun Microsystems and Patrick Chan for this code. Sun paid Xeo for its development, I believe, for use on the Java Web site.
The next line gives a background color to use in the transparent regions of the image. This particular example does not have any transparent areas, however the next one does.
The image to use is specified with the image parameter line. The VALUE can be any valid URL.
The seperator is a single character used to delimit fields in the menu parameters. The menu parameters are the last two PARAM entries which we'll cover in a moment. For now, just note that the seperator is used in the VALUE argument for the menu parameters.
Menu items can have multiple lines using this program. In order for XeoMenu to recognize a line break, the text uses a caret (^) to denote a newline. These are not used in these examples, but the caret would be embedded in the menu text in the menu parameters.
The next two lines specify the font and font height to use for the menu text. According to the man page for XeoMenu there are only 3 possible font types: Helvetica, TimesRoman, and Courier. This is probably a limitation in the early Java class libraries, but I'm not certain of that.
Marginh and marginv are used to pad the region around the menu text with empty space. The values are given in pixels.
Now come the text color parameters. First are the foreground and background colors to use for the text when the cursor has not been moved over the text, ie the default text colors. The latter two specify the colors to use when the cursor is placed over a menu entry. Note that in the first example the background colors are the same but the foreground colors are changed. This isn't a recommended method - the results are somewhat unappealing - but it does give you an idea of how the colors can provide variations of effects.
The last line before the two menu parameteers is actually commented out, but is given for the sake of completeness. This parameter is recognized by XeoMenu as the frame to display a menu items targe URL if it is selected.
Finally, we have the two menu parameters. XeoMenu recognizes any parameter prefixed with the word "menu" and suffixed with a numeric value as a menu item. This parameters value field contains a set of seperator delimited values that define the display location, contents, and URLs for each menu. The first set of 4 numbers is the hotspot. This is the region, specified by an x,y location and its width and height, in which the mouse must enter for XeoMenu to begin handling the menu features of the image. The next 4 numbers specify a secondary region of the image to overlay on the image when the mouse enters the hotspot. The next two numbers specify the offset into the image to place the overlay. In this example the offsets are specified so the overlay is place over the hotspot, blotting it out as it were. This is not the only way to use this feature, since the overlay can be placed anywhere on the image. Note that all of the x,y coordinates are given as pixel coordinates in the image.
After the offset comes a single character. This can either be a "d" or a "u". The "d" is used to post menus in a downward direction and the "u" draws them upward. The location of the upper left corner for the downward menus (and the lower left corner for upperward menus) is also the offsets specified for the overlay location (ie the two numbers that preceeded the "d" or "u").
Next comes the default URL. This is the URL that will be used if the user simply clicks in the hotspot without actually using a menu. After this comes the menu definitions. These are the text of the menu entries paired with a URL that follows immediately after it. Note that in the second menu parameter there is only one URL specified - the default URL. That means that no drop down menus are displayed when you place the mouse over the Gazette hotspot, but the overlay is still used.
In this next example, both regions of text use menus. One uses an upward menu and the other uses an overlay that is not directly over the original hotspot. Also, this image has a transparent region. Can you guess how to create this example? Try it first, before looking at the source code.
 |
| © 1998 by |
![]()
![]()
![]()
Next: Characteristics and chipset
Linux on a Kapok 7200
4.2.98 version 1.0
Alessandro Usseglio Viretta
Lab for EM 1
Schmelzbergstrasse 7, CH-8092 Zurich
e-mail:
Fax + 41 1 6321103
The Kapok 7200 is a portable computer, Intel-based, manufactured by Kapok - http://www.kapok.com.tw - in Taiwan. It is sold under a variety of names is USA and Europe. BSI http://www.bsicomputer.com, ATC http://www.at-computers.com, NewChip http://www.newchip.it, AJP http://www.ajp.co.uk, JET http://www.jet.ch, A&O http://www.aocomputer.com, Computer Direct http://www.direct.ch, Gericom http://www.gericom.com, Pro Star http://www.pro-star.com, Megashop http://www.megashop.ch are just a few vendors of this computer. It's a bulky and heavy computer, but it's provided with a big nice TFT screen - up to 14.1" - and a easily upgradable Pentium MMX processor. It is usually delivered with Windows 95 already installed. The aim of this document is to explain how to install Linux on such a machine. If you want to keep Windows, please refer to the HOWTOs available, for example, at http://sunsite.unc.edu/pub/Linux/docs/. This document is aimed to absolute beginners and is not intended to provide a deep insight into the Linux operating system. After reading it, the newby should be ready to successfully install a RedHat Linux system on his/her laptop and start working with it.
Only one hour after I taught my wife, Lois, how to access the Internet with our Macintosh Quadra 605, I knew that my dream of having a Linux-based home network would be realized. Surely, I reasoned, it would now be unacceptable for me to "hog" our Internet connection and prevent Lois from tracking down Star Trek Collector's Cards online. Fortunately I had used Linux IP Masquerading in a previous life as a LAN administrator and knew that a Linux solution would allow us both to be on the Internet at the same time with only a single modem connection and IP address from our Internet Service Provider.
There were a couple of constraints, however. First, there was no space in my family room for another computer; any additional system would have to be set up in the basement. Second, our Mac did not have an Ethernet card, nor was I inclined to pull Ethernet cable through my house. Third, any solution would have to be achieved on a shoestring budget (Did you hear the one about the guy whose wife had her credit cards stolen, and the guy didn't report it because the thief spent less than the wife?)
This article describes the Linux networking solution I came up with - it consists of my Mac, a Linux Box and a low cost dos-based router. It is not "state of the art", but it is a solution that works within the constraints I imposed, it is relatively simple, and it is one that many people haven't heard about before. As you will see, it heavily leverages software and information available on the Internet. Mac, DOS, and Linux users will all find something of interest in the material presented herein.
The remainder of this article is organized as follows: Section II presents an overview of my home network; Section III describes the network hardware and software; Section IV addresses setting up; Section V describes operations; and Section VI presents final comments, including things to try.
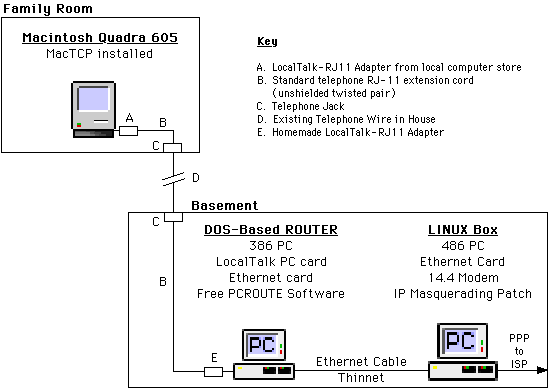
Figure 1 presents a schematic of my home network. My Macintosh (family room) has connectivity to my Linux box (basement) through a low cost dos-based router (also basement). The Macintosh-router segment is LocalTalk and the router-Linux box segment is Ethernet (thinnet). The Linux box provides the dialup PPP connection to my Internet Service Provider (ISP) and runs IP Masquerading which allows the Macintosh and the Linux box to use the Internet at the same time through the single dialup connection.
LocalTalk seemed the best way to establish connectivity between my family room (Mac) and my basement (PC's) for two reasons:
Some people might say that LocalTalk, at 230 KB/sec is too slow to be useful for networking. (Ethernet, in comparison, is 10MB/sec). However, my modem connection is only 14.4 KB/sec (57.6 KB/sec maximum throughput) making LocalTalk seem more than adequate.
Having a LocalTalk connection from my Mac to my basement still didn't help me connect to my Linux box. Linux does offer AppleTalk support, but it does not yet offer support for LocalTalk (although I understand the hooks for LocalTalk are now built into the AppleTalk code).
That's where the free router software, PCROUTE by Vance Morrison, comes in. PCROUTE is dos-based software available on the Internet (PCRTE224.ZIP at http://www.nova.edu/Inter-Links/simtel/network.html) that routes TCP/IP packets between LocalTalk and Ethernet networks. PCROUTE can run on a PC XT or better ( and it doesn't require an AppleTalk - IP Gateway like the LocalTalk packet driver-based routers such as KA9Q). Once PCROUTE is set up correctly, you don't even need a keyboard or monitor if your computer can boot without them. I run PCROUTE on an old 386 PC with 1Meg of Ram and a 5.25 inch floppy drive.
PCROUTE comes with excellent instructions on how to compile and configure it as a LocalTalk/Ethernet router. Of course the router needs both a LocalTalk PC card and an Ethernet card. The latter I already had and the former I bought for $27 + shipping from MacResource Computers, a Texas-based company I found on the Internet (http://www.mac-resource.com/mac-resource/).
Some more comments about the LocalTalk connection between my Mac and the router. To use phone lines for LocalTalk, both my Mac and the router required LocalTalk/RJ-11 adapters. The 8 pin mini-din variety is available at any computer superstore, however, the LocalTalk PC board required the older 9 pin variety. Those are easy enough to find for sale on the Internet, but I found the circuit itself on the Internet instead (http://www.jura2.uni-hamburg.de/~kai/LAM_HTME/cap1.htm)! It turns out that you can build the 8 or 9 pin variety with only 5 resistors, 2 capacitors, and some miscellaneous parts - and it all fits in a 35mm film canister! I built one for my router and it works great. (One word of caution - the pinouts for the 9 pin adapter or left/right backward in the figure provided with the circuit.)
I have a single phone line in my house; it uses the inner red and green wires of the modular phone plug for the telephone connection. The outer black and yellow wires are available for LocalTalk. Fortunately, LocalTalk/RJ-11 adapters are already wired to use the outer wires.
My Linux box is a 486DX33 PC with 16Megs of Ram, a 270MB hard disk, and a 14.4 baud Modem. It uses a thinnet Ethernet connection to the router. The only unusual part of installing Linux was that my 486 does not have a CD-ROM drive. To load the Linux software, I decided I needed to get the software on the DOS partition of my 486 so I could install Linux from there.
To accomplish this I temporarily installed the LocalTalk PC card in the 486 and loaded the software that came with the card. The software allows you to mount Macintosh folders as letter drives (e.g. f:) on your PC. I simply copied the Linux installation software off the CD-ROM into a folder on my Macintosh hard disk, mounted that folder over the LocalTalk network as drive f: on the 486, and used XCOPY to move all the LINUX software to my 486 (e.g. XCOPY f:*.* c: /s /e).
I followed RFC 1597, which allocates certain IP addresses for private networks, and internally assigned 192.168.1.x for my LocalTalk segment and 192.168.2.x for my Ethernet segment. In the next three sections, I provide specific instructions for configuring the network.
The Macintosh setup is straightforward. Select MacTCP from the control panel. In the first MACTCP window, select the "More" button. In the second window, set the server to "Manual" and the gateway IP to 192.168.1.1 (This is the IP address for the router's LocalTalk PC card). I leave the DNS servers the same as I use to access the Internet directly with my Mac's modem.
Click "OK" to return to the first MacTCP screen. On the first screen, change the Mac's IP address to 192.168.1.2 and select the LocalTalk icon. Make sure that LocalTalk is turned on in the Chooser.
PCROUTE comes with excellent documentation which I will not repeat here. I set up the LocalTalk interface with an IP address of 192.168.1.1 and the Ethernet interface with an IP address of 192.168.2.1. For the Ethernet interface I have successfully compiled and run two different configurations of PCROUTE, one that uses a direct interface to an 8 bit WD8003 Ethernet card and one that uses an Ethernet packet driver interface. The nice feature of the packet driver interface is that it allows you to use any Ethernet card for which a packet driver exists. I have successfully used PCROUTE with both the WD8003 card and a 16-bit NE2000 compatible card using packet drivers.
In the router, I set a static default route to 192.168.2.2 (the Linux box) so that any IP address not recognized by the router (e.g. www sites from my Mac intended for the Internet) will be routed by default to the Linux box.
A neat feature of PCROUTE is that it allows you to designate the Linux box as a syslogd host that logs status messages from the router. When the router starts up, and approximately every 15 minutes thereafter, the router sends the Linux box a "Router is up" message that is recorded in a file on the Linux box that you specify.
I set the IP address for the Linux Ethernet interface to 192.168.2.2 and designated the router (192.168.2.1) as the gateway for packets addressed to the LocalTalk segment (192.168.1.x).
To log syslog messages from the router, edit the /etc/syslog.conf file as described in the PCROUTE documentation. Then reboot Linux or type kill -HUP <pid>, where pid is the syslogd process id obtained by typing ps -x.
As stated earlier, I use IP Masquerading to give my Mac and Linux box simultaneous access to the Internet through a single PPP connection to my ISP. However, because I use Linux 1.2.13, the IP Masquerading capability has to be built into the kernel as a patch. Fortunately, IP Masquerading comes with excellent instructions for applying the patch.
To configure IP masquerading, I use:
ipfw a m all from 192.168.2.0/24 to 0.0.0.0/0 ipfw a m all from 192.168.1.0/24 to 0.0.0.0/0
These steps will automatically masquerade my Mac and any future computer I add to either my LocalTalk segment or my Ethernet segment. If you don't want to retype these lines each time you reboot your computer, add the steps to one of the startup scripts executed from the /etc/rc.d directory.
I will not describe setting up a PPP connection from my Linux box to my ISP; good instructions are already provided in the Linux How-To documents. When the PPP link is up and running and IP Masquerading is set up as described, my routing table (obtained by typing "route -n") looks like:
Destination Gateway Genmask Iface 207.96.96.102 * 255.255.255.255 ppp0 192.168.2.0 * 255.255.255.0 eth0 192.168.1.0 192.168.2.1 255.255.255.0 eth0 127.0.0.0 * 255.0.0.0 lo default 207.96.96.102 * ppp0
My setup works great! I can initiate a PPP connection to my ISP by logging into my Linux box, either by walking down the basement, or telnetting to the Linux box from my Mac. Best of all, thanks to IP Masquerading, my wife and I can now both use the Internet at the same time!
With my new LAN setup, my Internet programs (e.g. my web browser) run slightly faster now because my Mac no longer has to simultaneously maintain a modem connection and run MacPPP. Further, when I have to reboot my Mac (yes, it does happen occasionally with Macs) I don't have to redial my ISP because the connection is maintained by my Linux box; as soon as I reboot, I'm back online.
I have not tried to optimize the performance of my Mac-Linux LAN. However, since Ethernet packets can be almost 3 times larger than LocalTalk packets, one thing to try is to move the burden of reducing the packet size from the router to the Linux box by reducing the MTU parameter of the Linux Ethernet interface. (For example, to change the MTU size to 500, type "ifconfig eth0 mtu 500.") Another interesting thing to try is IRQTUNE which lets you give the serial port on the Linux box higher processing priority so that it has less chance of dropping packets (http://www.best.com/~cae/irqtune). I have not tried IRQTUNE yet, but it might be a good thing to run for anyone using a modem with a Linux box.
One of the things I'd like to try is accessing my Linux box using X-server software on my Mac. I'll have to make sure that the X-server software can run over LocalTalk.
This article has described a low cost way of creating a Mac - Linux network at home. I hope that Mac, DOS, and Linux users have all found something of interest in the setup I've described.
I would be happy to hear from anyone with comments or questions.
CD-players for Linux abound these days, with both curses-based console programs and X programs available in a variety of degrees of usefulness, complexity, and polish. There are even command-line players, though with the current CDROM drives (with their built-in controls) a player is no longer strictly necessary. The main advantage of using a dedicated CD-player program is the possibility of using a database containing titles and track names, as well as play-lists, auto-repeating and other user conveniences.
Xmcd is one of the more popular X-windows players; it's a freely available program but does require the proprietary Motif libs for compilation from source, though statically-linked binaries are available. One reason for its popularity is the internet database of CD titles and tracklists which is accessible from within the program. This database is remarkably complete, and once you start using it only the most obscure titles should ever have to be entered manually. This database project has really mushroomed; originally Ti Kan (author of Xmcd) created the database format for use in his program, and distributed database files made up of user contributions. The files began to become excessively large and cumbersome, so the idea of making them directly accessible via the internet arose. Ti Kan recruited Steve Scherf to write a protocol which would make possible quick retrieval of individual queries, and Steve found sites which agreed to become servers. There are now CDDB servers distributed across the planet, and the databases are even accessible from behind firewalls from many HTTP servers. Information on incorporating the protocol into a CD-player program is available from the cddb website; this material is freely available, and assistance is offered for freeware and shareware developers.
Unfortunately, I never have been able to get Xmcd to work consistently on my system; there is something in the way my ATAPI drive works which causes problems. Xmcd was originally written with SCSI drives in mind, and although ATAPI IDE drive support has been added it didn't seem to care for my drive's peculiarities.
I've been using Tim Gerla's simple but useful console-mode player tcd for several months, and have become quite adept at quickly typing in disc and track information. Recently Tim introduced a new version. and after unpacking it I was surprised and pleased to see that not only had he produced a GTK-based X version, but the program now supports the CDDB protocol. So one day I was on the internet, downloading some beta software, and started up the new tcd version. I was playing a disc which I hadn't entered into the program's database, and I happened to see a notice on the screen which said "[D] Download CDDB data". I gave it a try, thinking that it would probably take awhile, and that the particular CD I was playing probably wasn't even listed. Within two seconds the title and track data was displayed on the screen, which startled and impressed me.
This newly released version, 2.0b, is a beta, though I haven't encountered any but the most minor bugs. The GTK version doubtless will be revised, as GTK is still under active development. Here's a screenshot of the interface:
It's a nice-looking interface, with that distinctive GTK look made familiar by the Gimp. When the CDDB button is clicked a window opens with the default server and port displayed in entry fields, which can then be edited depending on your location. A convenient drop-down menu of track titles (invoked by clicking the Goto button) is a feature not found on many players.
Most of tcd's features can be found on other X-windows players, though the only others which are CDDB-enabled (as far as I know) are Xmcd and the KDE CD-player Kscd, written by Johannes Wuebben. The last-mentioned is a very usable and well-done application, but requires the KDE and Qt libraries in order to function. Gtcd only needs gtk+-0.99.3, which is also needed by the Gimp.
An unusual feature is the existence of both console and X executables which share the same features, configuration, and database. I use X about two-thirds of the time, shutting it down when I'm compiling large applications or just writing in an editor, and it's nice to be able to use the same CD-player in each environment.
As I write this, the source and binary distributions are still in the incoming directory at Sunsite, with the filenames prefixed by tcd-2.0b; an alternate site is here.
Well, this article covers a couple of topics that you've probably seen discussed before in Linux Gazette and/or Linux Journal. Let's say you have 2 or more computers, maybe in an office, maybe at home, and you want to have one of them be the "gateway" for the other(s). If your ISP charges by the minute (or in 5/10/15 minute increments), which many of them do for corporate accounts, then you don't want to spend excessive amounts of time on the line to your ISP. You also don't want to risk forgetting that you are connected and running up a bill while doing nothing! So what you want is a way to get your local network onto and off of the Internet with ease, and with a minimum of extraneous cost. This includes demand-dialing, IP forwarding, IP Masquerading, PPP configuration, and some basics of networking. Sounds like a lot (and believe me, it can be!), but it's not so bad when you find out that, for the most part, you don't necessarily need all the power and flexibility that the packages involved in this setup have.
Please note that while I will be detailing how to set up your Internet gateway in Linux, that does not imply that your entire network needs to be running Linux. You can have one Linux box acting as the gateway, while the rest of the network is a mix of other platforms. You can have any kind of hardware and software on the network, provided that the systems have a TCP/IP stack. Any mix of DOS, Mac, Win95, or unix workstation can be applied to a network configured in this way.
This kind of arrangement is extremely useful for a number of reasons. If WWW browsers are going to be used heavily, this kind of network is ideal. WWW browsers open transient TCP connections for operation, which download chunks of information in spurts, usually not remaining connected for more than a few seconds. While someone reads a web page, the browser generates no (or very little) network traffic, thus leaving the connection idle, and allowing someone else to share the unused bandwidth to full potential. Another reason for installing this kind of arrangement is so that users don't tie up valuable phone lines for extended periods. Recently, I installed a similar arrangement for a small company whose employees were frequently on the Internet from their PC's, each using their own phone line at their desk. Of the few and costly phone lines they had, usually half of them were doing dial-up connections, while the other half could handle voice calls. By the arrangement that I prescribe here, they limited it to one phone line, and everybody was able to access the Internet while using the phone line at their desk for voice.
To describe what I've done here, I'm working from the reference frame of having installed a fresh copy of Red Hat 4.2, with the option of installing everything set. From what I've seen, 5.0 isn't incredibly different (for this stuff, anyway), and I'll also be pointing out the differences between setting this up on Red Hat and setting this up on Slackware 3.3.
First and foremost, I would recommend some other documents for your perusal before engaging in setting up a working LAN. These would be:
I will be using the term "Linux gateway" or "gateway" to denote the machine on your network which will be running Linux and actually have the modem and will be performing the connections to the outside world for your network.
Networks for small offices or within a home are generally not in registered domains. If you are setting up a connection for an office which is in a registered domain with an IP address which is part of the Internet (ie, not one of the reserved network numbers for private use), then you will need to configure your network according to that registered domain and IP address block which you have been allocated by InterNIC. If you don't know what I'm talking about, then you want to use one of the "reserved" network numbers that are set aside for private usage. The network number which I will use will be "192.168.1.0", which I have configured for my home usage. Because it's reserved, I know that all my packets will not conflict with anyone on the Internet, since all packets destined for reserved addresses are dropped by your ISP's routers, and the main backbone routers on the Internet.
Note that the steps I describe here are often done in parallel with the previous section on "Have a Working Network". Once you've selected a reserved IP address block for your network, you need to configure your hardware to be recognized and give the appropriate parameters to the software. I recommend setting the gateway's address to the ".1" node number of your network. It's not a law, but it's commonly accepted and easy to remember. For example, if you are using 192.168.1.0 as your network, then 192.168.1.1 will be your Linux gateway. Then have the other systems on the network numbered as 192.168.1.2 through 192.168.1.254. Some administrators like to have their nameserver for the LAN set up as ".254", but if you only have a few machines on your network, you're not likely to need or want a nameserver.
Selecting a domain name doesn't deserve a huge amount of thought. It's just a matter of coming up with something that is easy to remember, describes your network, and will not conflict with any registered domain names. The extensions of ".com", ".org", and ".edu", as well as country abbreviations (".de", ".uk", ".au", etc.) are off-limits. Just don't use anything that looks like a typical address, and you'll be ok. For example, my local network at home is the domain of "kunz.home". There's no domain out there belonging to ".home", so it's OK. Or if you want to set up an office network for "ACME Inc.", then you might try "acme.office" as your domain name.
The network parameters can be set up in Linux either while performing the initial installation or after the installation has been done. If you decide that you would like to have your gateway named "linux-gw", and that you want your domain to be "smith.home", you will not have any conflicts with names outside of your network. If you are using 192.168.1.0 as your network number, then the parameters for networking should look like this:
Also, notice that it's important to leave the default gateway empty! The routing tables will be modified by diald, which will be discussed later.
On "linux-gw", you should make/edit the /etc/hosts file. It should contain the IP addresses and names of all the machines on the network. Let's say you will have 4 machines on the network besides the Linux gateway. You might, conceivably, have an /etc/hosts file that looks something like this:
127.0.0.1 localhost localhost.localdomain 192.168.1.1 linux-gw.smith.home linux-gw 192.168.1.2 winchester.smith.home winchester 192.168.1.3 ruger.smith.home ruger 192.168.1.4 browning.smith.home browning 192.168.1.5 mossberg.smith.home mossbergBy doing this, the Linux gateway knows the names of all the machines on the network. This should also be done on any unix workstations or other Linux machines you have on the network. On Slackware installations, you'll need to edit this by hand. On Red Hat, you can use the "netcfg" program under X to modify the "Hosts" entry.
On each of the other machines in the network, you will need to configure their parameters as follows. Be sure not to duplicate IP addresses between different machines! The following sample entry is for a client on the "smith.home" network named "winchester".
If you are configuring a Slackware Linux machine as your gateway after installation, the appropriate way to change the network parameters is to run the program "netconfig" as root. You will be prompted for the network parameters one at a time, and should follow the "linux-gw" listing above. Under Red Hat, you should run the "netcfg" program from X while root. This provides a graphical tool for doing the same thing. Running "control-panel" as root in Red Hat provides an X front-end to many of the administrative tasks, including networking.
By the time you get this far, you should have a working network, where you can telnet from any of the machines on your network into the Linux gateway.
The package that we will be using for performing the automatic dialling is "diald". This assumes that you have a modem which Linux is already aware of. If not, you need to consult your installation documentation and the incredibly useful Linux Resources page
Once you can verify that your modem is working ok and is recognized by Linux correctly, we can configure diald to do the work for us. As a note, I would like to say that I've had the least problems with external modems and with non-PnP modems. These days, it's hard (if possible at all) to find a non-PnP internal modem. If you absolutely have to use a PnP modem, then I recommend getting the isapnptools package for initializing PnP configuration.
First, you need to obtain and install diald. If not already installed on your system, it's possible to obtain the code from Sunsite. If you have Red Hat, you can find the binary distribution in RPM format on your Red Hat 4.2 CDROM. It is located in /[mountpoint]/RHSCont/i386/diald-0.16-3.i386.rpm. The file diald-config-0.1-1.i386.rpm is found in the same directory, and I recommend you install it, since it contains some sample configurations that may be useful to you. Under Red Hat 5.0, I was unable to find it on the 2-CDROM distribution set from Red Hat, so the latest version of diald should be downloaded from Sunsite. The same goes for Slackware. Download the pacakge and follow the build instructions included. [LG HTML note: if you find those links are broken by the time you read this, you should be able to browse http://www.sunsite.unc.edu/pub/Linux/system/network/serial/ to find the current version of diald]
Once you have diald installed, we need to install pppd. This comes up in both Slackware and Red Hat 4.2/5.0 as packages that are selected for installation if you install everything. If it is not installed, it can be found on your Red Hat 4.2 CD in /[mountpoint]/RedHat/RPMS/ppp-2.2.0f-3.i386.rpm. If you have RedHat 5.0, you will find it on the first CD of the set, in /[mountpoint]/RedHat/RPMS/ppp-2.2.0f-5.i386.rpm. Slackware contains the ppp.tgz package at or around floppy N3 or /[mountpoint]/slakware/n3. If you don't have it installed on your Linux gateway already, you may need to download the source for it from Sunsite. Basically, just follow the build instructions and install it via the Makefile.
Now you have diald and pppd installed, but you may not have any support for IP Masquerading, which is an absolute MUST for this kind of networking scheme. If you are using a stock Red Hat 5.0 kernel, you will be fine, as just about everything is compiled as a module. IP forwarding will be provided on-demand by kernel module loader, as long as you have modified /etc/sysconfig/network (see "Configuring IP Forwarding Firewall", below). If you're using a stock kernel that came with Slackware, you probably don't have support for the IP Masquerading ready. If you installed everything as I recommend in the beginning, you'll have the kernel sources already on your Linux gateway. But if not, you can download the source code for kernel 2.0.33 from Sunsite. Be patient! It's a 6M file!
Just untar it in your /usr/src directory, and the do the following:
The next step along the path to having a Linux machine that can act as a gateway to the Internet is to configure IP forwarding. IP forwarding can be a very complicated and involved thing, however, to act as a simple gateway and firewall to the Internet, all we need to do is configure the forwarding rules so that packets of all types found on the ethernet interface are copied onto ppp interface.
Please be aware that you should be fully informed of the security concerns of this. I recommend that you read some materials on security, keep a copy of SATAN handy, and consult some security experts if you worry about security. If you have a dial-up service to a local ISP, there is a lower probability that you will be hacked on than if you are using a university as your ISP. College kids aren't necessarily malicious, but they can be deemed a security risk, as they are usually more "inquisitive" than the typical Windoze 95 user at home who happens to be a customer of your local ISP. Don't take me as Gospel Truth, check into it for yourself and find out the issues about security if it is something you want to know about.
The first thing to have is the ipfwadm package installed on your system. If you have it already installed and your kernel has been compiled in the previous step to support packet forwarding, then you're set, and you can move onto the actual configuration of the firewall. If you are using Red Hat 4.2, the package can be found at /[mountpoint]/RedHat/RPMS/ipfwadm-2.3.0-2.i386.rpm. If you are using Red Hat 5.0, you should find it on the first CD of the set, in /[mountpoint]/RedHat/RPMS/ipfwadm-2.3.0-5.i386.rpm. If you're using Red Hat, you will note that you'll also have to modify the file /etc/sysconfig/network, making the line containing "FORWARD_IPV4" to say "FOWARD_IPV4=true". For Slackware, you should find installed in the base TCP/IP package (N6, "tcpip.tgz"), so if you have TCP/IP networking installed, it should already be there. If you need to download it, the source can be found at its home page.
Once you have the package installed, you need to know how to use it! Depending on how secure you would like it to be, you can make a few changes to what I have here. What you want to do is flush the table of all previous firewall forwarding entries, set a default policy for either accepting or rejecting packets, and then tell it how to forward packets between different interfaces. For example, the following script will flush all forwarding rules, set the default policy to "accept" packets, and will forward packets between all of the available interfaces:
#!/bin/sh ipfwadm -F -f ipfwadm -F -p accept ipfwadm -F -a m -S 192.168.1.0/24 -D 0.0.0.0/0We can view the IP forwarding rules by issuing the command "ipfwadm -F -l -n", which will list the rules numerically. If we do that, we will get output looking like this:
IP firewall forward rules, default policy: accept type prot source destination ports acc/m all 192.168.1.0/24 0.0.0.0/0 n/aThis tells us that any packets going from our network to anything other than just our network will be forwarded between all of the interfaces. Now, if we specify an additional "-e" option to the previous command, we get extended output of the forwarding rules. This is to our advantage, but you should have a 132 character wide screen when you run it. Here is a sample output:
IP firewall forward rules, default policy: accept
pkts bytes type prot opt tosa tosx ifname ifaddress source
destination ports
113 9452 acc/m all ---- 0xFF 0x00 any any
192.168.1.0/24 anywhere n/a
Thus, we can see that even though IP forwarding can be incredibly complicated and selective, we can write a simple script which will do all the work for us and establish a forwarding firewall.
If you read the manpage for ipfwadm, you will find that the -W option may be used to specified. For simple situations and a simple network in a generally trusted environment, the -W option isn't necessary, because you are probably interested in having all interfaces able to see all packets. However, if you are interested in keeping certain interfaces from receiving packets, you may use the -W option for security.
The first thing we want to do is configure pppd, because it's often easier to test out than diald. To do this, we want to create a chat script, which will dialog with the ISP, and establish the connection. You will want to read the man page for "chat" first, but here is an example of a chat script I use:
REPORT CONNECT ABORT BUSY '' atdt5551212 CONNECT '' : tkunz : PaSsWoRd action ppp>From the manpage:
This sequence will expect nothing; and then send the
string ATDT5551212 to dial the telephone. The expected
string is CONNECT. If the string CONNECT is received the
remainder of the script is executed. In addition the pro-
gram will write to the expect-file the string "CONNECT"
plus any characters which follow it such as the connection
rate.
First, the script will report what the modem returns after "CONNECT" into the report file, to be analyzed later, in order to diagnose what could have gone wrong with the dial-up. The ABORT string means to abort the script should it see the "BUSY" string returned by the modem. After that, this script will diald "555-1212" as the phone number, and wait for the CONNECT message to come back from the remote end. It will then wait for a colon (":"), and reply with "tkunz". It will wait for another color (":"), and reply with "PaSsWoRd". When the string "action" is received from the remote end, it replies with "ppp" and the chat script terminates. Chat will then pass control back to the program that called it. But here's another script that will work fine, provided we don't need the "REPORT" error checking, and we don't ever expect to get a busy signal:
atz OK atdt5551212 CONNECT name: tkunz word: PaSsWoRd action: pppThis one will do the same thing, only it will initialize the modem to the default setting by issuing "atz" first, and instead of expecting only a colon, it waits for "name:" and "word:" to be received before issuing "tkunz" and "PaSsWoRd", respectively, to the remote end.
These simple one-line scripts like the above examples can be used with chat to automate the login procedure with your ISP.
pppd uses chat to establish a connection, and then when chat terminates, pppd continues to dialog with the remote end, determining its local and remote IP addresses, and then pppd follows the other command line options to secure a reliable connection.
To give you an idea of what a set of scripts would look like that starts a PPP connection, here is a sample of something I use to manually bring up a PPP connection to my ISP.
The contents of a file in my own directory, named "startppp":
#!/bin/sh /usr/sbin/pppd /dev/cua3 115200 connect 'chat -f /etc/ppp/chatscript' defaultroute crtscts proxyarp passiveThis tells pppd to use my modem, located on /dev/cua3 (COM4 in DOS), at a speed of 115200, which my 33.6kbps modem can handle. The "connect" parameter says to use the next quoted string as the command-line which will connect pppd to the remote host.
The option "defaultroute" tells pppd to modify the routing tables so that this connection is added as a default route to the rest of the world. The "crtscts" option tells pppd to use hardware flow control for the modem, a MUST for modems faster than about 9600 baud. "proxyarp" says to add an ARP entry for the local and remote systems to the ARP table. The "passive" option tells pppd to be patient about receiving LCP packets from the ISP. If pppd does not immediately receive an LCP packet from the remote end, it drops carrier. I have personally found this to be the "magic ingredient" to getting pppd working with several different ISP's. The contents of the file /etc/ppp/chatscript, used by "chat" in "startppp":
REPORT CONNECT ABORT BUSY '' atdt5551212 CONNECT '' : tkunz : PaSsWoRd action pppSubstitute in your login name, password, and the command which starts ppp (if any) for the appropriate fields in the /etc/ppp/chatscript, and see what happens. You may need to contact your ISP if you have never used pppd in Linux before to establish a PPP connection, to determine if there are specific options necessary to make and sustain a PPP connection. You can try the above script and then watch the /var/log/messages file to see what happens. You might need to modify your /etc/syslog.conf file to get the messages printed to the right location if you use Red Hat. I prefer a slightly modified Slackware /etc/syslog.conf, which is shown here:
# /etc/syslog.conf # Very Important! All whitespace are TABs, not " " (space) characters! # *.=info;*.=notice /var/log/messages *.=debug /var/log/debug *.warn /var/log/syslogAfter making this your syslog.conf file, you can do a "touch" on /var/log/messages, /var/log/debug, and /var/log/syslog, restart syslogd and watch the messages appear. Occaisonally, I've noticed strangeness with syslogd not wanting to give up the previous configuration, so you might find a reboot rather than just a restart of syslogd is in order.
Once you have syslogd logging the right level of messages to the locations mentioned above, you can watch the progress of pppd from one window or virtual console while you execute "startppp" from another. By watching /var/log/messages (and possibly by watching the modem lights if you have an external modem), you can determine if chat succeeded or failed, or if the right options were specified to pppd. As root, the command "tail -f /var/log/messages" will enable you to see messages as they are dumped into /var/log/messages.
By experimentation, you should be able to get a PPP connection started by using these scripts and commands. Again, I mention that you might have to call your ISP to find out if any special LCP or IPCP options need to be set.
By this time, you should be able to regularly initiate a PPP link to your ISP by executing "startppp", and you should be able to use web browsers and the like to get onto the Internet from the other machines on the network once you have the IP forwarding rules installed. The next peice of the puzzle is diald. diald is designed as a demand-dialer, meaning that when it senses that you want to get from the local network out onto the Internet, it dials your ISP and sets up the connection for you.
The first thing to realize is that we are going to have to change the way we think about pppd and chat for the moment. Before, in our previous script in the section about configuring pppd, we had pppd start up, then issue the "connect" command. After that occurred, pppd would run according to the options we put on the command line. In diald, we have to recognize that diald will be handling many of the details that pppd handled before. These details include the dialing script and options that would normally be passed to pppd. diald will be responsible for implementing these things now, not pppd.
What diald does is it creates a "virtual" interface, sl0, which is a slip interface to nowhere. We will have it assign the IP address of 192.168.0.1 to sl0, and an IP address of 192.168.0.2 to the remote end (basically nothing!) of the fake slip interface. Then it creates a route so that traffic not intended for the local network will go into sl0. When diald finds packets being copied onto sl0, it realizes that those packets should go into the Internat, and starts the dialing process. In order to make our particular network arrangement work, we have to set up the IP forwarding to be promiscuous, in a sense, in that it forwards between all interfaces, including sl0. Thus, packets which are generated by one of the other machines on the network will go into the Linux gateway, the IP forwarding mechanism will copy them onto the sl0 interface if they are not destined for only the local network, and then diald will take over, starting the dialing process and pppd to bring up the link.
The manpage of diald-examples should have been installed on your system when you installed it. If you read that, you will probably find your own situation there in the manpage, however, most of you will probably find that it corresponds with the section named "A Leaf Node with Dynamic Local Address using PPP". The following comes directly from the diald-examples(5) manpage for this situation:
mode ppp
connect /etc/diald/connect
device /dev/ttyS1
speed 115200
modem
lock
crtscts
local 192.168.0.1
remote 192.168.0.2
dynamic
defaultroute
include /usr/lib/diald/standard.filter
To start off with, you should have the above as your initial /etc/diald.conf file. We will add options to it later. At this point, please understand that diald has to know exactly where to find the external programs of route, ifconfig, and pppd. This article assumes that you have installed pppd, ifconfig, and route into their default locations, which are:
/usr/sbin/pppd
/sbin/ifconfig
/sbin/route
If for some reason you do not have them installed in the above locations, please make links or move them to the appropriate locations.
Now we come to the part where we modify that initial /etc/diald.conf file. First of all, we have created a working chat script in an earlier part of this article, "Configuring pppd". Using that information, we modify the lines starting with "connect ...", "device ..." and "speed ..." to reflect your configuration. If you followed my directions exactly in "Configuring pppd" and have a 33.6kbps modem on COM4 like I do, then you would get a diald.conf that looks like this:
mode ppp
connect "chat -f /etc/ppp/chatscript"
device /dev/cua3
speed 115200
modem
lock
crtscts
local 192.168.0.1
remote 192.168.0.2
dynamic
defaultroute
include /usr/lib/diald/standard.filter
Note that if you have a 28.8k, 33.6k, or 56k modem, your "speed ..." line will look the same. If you're using a 14.4k, you'll most likely have to use "speed 57600". Also, make sure you use the correct number of the COM port. COM ports in DOS are one higher than the appropriate cua number, since DOS starts numbering from "1" and unix tends to number things starting from "0".
One thing to note about the diald.conf file is the set of options which would normally have been specified to pppd. According to the diald manpage, you must not specify those as direct options to pppd. This is one of those details handled only by diald. In our original "startppp" script, we specified "... defaultroute crtscts proxyarp passive". In our new situation, using diald instead of pppd to manipulate those options, we need to set those here in diald.conf. All but the "passive" option can be specified. Thus, we get a diald.conf that looks like this:
mode ppp
connect "chat -f /etc/ppp/chatscript"
device /dev/cua3
speed 115200
modem
lock
crtscts
local 192.168.0.1
remote 192.168.0.2
dynamic
defaultroute
proxyarp
include /usr/lib/diald/standard.filter
If we need to add the "passive" command to pppd to make it work with your ISP correctly, then we can insert a new line into the above of the form:
pppd-options passive
The above diald.conf should get you started with a working connection to your ISP. If not, you may need to consult your ISP's technical support line to find out what they recommend.
At this point, you should be able to start diald and watch the messages in /var/log/messages appear which it generates upon start-up. After diald starts, you should also be able to send packets from other nodes of your network to the Internet, and then watch as diald automatically dials out and establishes a connection. If not, go back over the previous steps to find out what went wrong.
There are also important variables which are not associated with the link uptime itself, but with the time that different portions of diald take to execute or time-out. For example, if dialing your ISP and passing the username, password and related actions take more than 60 seconds, typically, you will want to add a line to the file that says something like:
connect-timeout 120
Or, if you wish to have diald attempt a redial 10 times before giving up and only wait 15 seconds to clear the modem between dials, you will want to add in the following two lines:
retry-count 10
redial-timeout 15
You may also wish to play with some of the other options that diald has to offer. For example, one option that can be useful is "two-way". This tells diald that if carrier is dropped while in operation, that it will not retry dialing. What good is that? Well, if you have to forcibly terminate the PPP connection to your ISP (killing off pppd manually to free the line, physically pulling the phone line connection, etc.) diald will not try to outsmart you and dial again. If you have a somewhat dedicated line, and you are not concerned about how long you are connected to your ISP, you won't need that option very much, as you'll probably stay connected for longer periods of time.
If you are concerned with accounting for the time that is spent online, then you will want to play with the "accounting-log ..." option. The parameter to "accounting-log" should be the full pathname of a file which will log the times when the link comes up and goes down, and how much data was sent down the wire. But I said I wouldn't spend any time talking about accounting and logging ...
The diald manpage is rich with options, and I would recommend that you read it in parallel with reading this article. Diald is wonderfully configurable, and can meet a wide variety of needs, depending on how complex of an arrangement you wish.
OK! Now you can go to any node of your network, start up {Netscape, IE, Arena, Mosaic, any browser} and get to somewhere out on the rest of the Internet. However, why does it seem like sometimes your Linux gateway almost randomly fires up a connection? What's it doing?
Well, now you need to delve into the particular applications on your network and how they're configured. Two of the big things to check are mail client and web browsers which contain mail clients. If your mail client makes requests for new mail, it will generate a packet which goes to your gateway, and initiates a call. This means that while the Internet connection is down, someone with a mail client up and running somewhere on your local network can unwittingly cause the gateway to establish a connection. This can be annoying and/or costly, both for the typical home user and the corporation. I know that I've accidentally done this to my wife on a number of occaisons, where my gateway attempted to dial out while she was on the phone with someone! (But she's a wonderful, patient, forgiving wife.)
To fix this, what you need to do is to inform your staff (or family) that once they finish with their mail client, they should terminate it immediately. And they should also be informed that they should turn off the automatic mail-fetching for any mail client that they use, especially if you are billed for connection time to your ISP or per minute of call (European countries often bill for even local calls).
Another thing to watch out for is the /etc/resolv.conf on the unix hosts on your network. You must not have any nameservers which are outside of your local network listed in it, or else every application that accepts a hostname will generate packets and cause your gateway to dial out. For this reason, it's wise to keep every hostname your local network needs in /etc/hosts on each unix machine. If your local network is large enough to warrant the effort, you might also set up your own local nameserver to handle the name requests. A local nameserver with its own maps for the local domain, and a caching nameserver for outside requests is probably the most efficient way of handling that. If you are going to be using a local mail agent like sendmail, then you will want to be sure to configure it in such a way that it will not cause the gateway to dial-up the ISP at every instance of outgoing mail. You'll want it spooled until a connection is available, or at a routinely scheduled time when all queued mail will be transmitted out.
Obviously, this document is not going to go into any detail about how to configure the various applications on your network around using a demand-dialed gateway. It is useful, however, to be aware of some of the issues you will face when you add different applications and platforms to your network, and why things may not be going the way you initially supposed they would. If you are faced with a larger network which requires greater upkeep in order to keep it working right, and high bandwidth to the Internet on a regular basis, it may be time to consider investing in faster connections (ISDN, T1, T3, OC3, etc.) and leased lines which better suit your needs. Note that diald can work with ISDN, but in a larger-scale network with higher bandwidth demands, a full-time connection may be the best solution.
Well, it's seems apropriate to say that configuring a small network with demand dialing via diald is a task which can be quite involved, depending on the complexity of your network. But if you have fairly "ordinary" needs, you can follow the above procedures to get a working and reliable demand-dialed connection. Many, at this point, will say "Well, what are 'ordinary needs' anyway?" or "How big of a network will this support?". The answer is subjective, however I can say with reasonable certainty that a network of 2 to 8 machines, each running their own web browsers, mail clients, and the like, will be quite adequate over even a 28.8kbps modem. The connection I get to my local ISP rarely gets past 28.8kbps on my 33.6kbps modem, because of the lines in my area, and often drops down to 21.6kbps or so, yet I still get reasonably quick response from having 2 or 3 machines accessing the Internet simultaneously. If you lust for speed, then you will do well to get a 56kbps modem, and a line to your ISP that can sustain 56kbps (yes, 53k download by FCC law). From my experience, diald will have no trouble with a 56kbps, provided it is either external and connected to a 16550 UART, or if you have built some version of a PnP configuration manager which can reliably configure an internal 56k modem.
Linux leverages a vast amount of academic software, either easy ports of existing Unix packages or, increasingly in recent years, software that is already ready to run under Linux. One example is Yorick, and this article is an attempt to provide a brief overview of the nature and capabilities of this system.
Yorick is not just another calculator -- readable syntax, array notation, and powerful IO and graphics capabilities make Yorick a favorite tool for scientific numerical analysis. Machine-independent IO, using the standard NetCDF file formats, simplifies moving applications between hardware architectures.
Yorick is an interpreted language for numerical analysis, developed at Livermore Labs by David H. Munro. Implemented in C, it is freely distributed under a liberal copyright. Yorick runs on a vast range of machines, from 486SX Linux Laptops (in my case) to Cray YMP supercomputers.
Who uses Yorick? The majority of users are physicists, many with access to the most powerful computers in the world. Specific applications include Astrophysics, Astronomy, Neurosciences, Medical Image Processing and Fusion Research.
In this article I will discuss the basics of running Yorick, describe the key array operations, and briefly discuss array operations, programming, and graphics. I hope that this quick look is enough to get the more mathematically inclined of you to give Yorick a try.
When invoked without arguments, Yorick presents a typical command line interface. Expressions are evaluated immediately, and the result is displayed. Primitive types include integers, floating point values, and strings, and all the built-in functions and constants you would expect are present.
Variable names are unadorned -- no leading $, and need not be pre-declared, and C style comments are supported.
One might not expect an interpreted language to be suitable for numerical analysis -- and indeed this would be the case if arrays were not built into the language. Arrays are first-class objects that can be operated on with a single operation. Since the virtual machine understands arrays, it can apply optimized compiled subroutines to array operations eliminating the speed penalty of the interpreter.
Arrays can be created explicitly:
> a1 = [1.1, 1.2, 1.3, 1.4, 1,5]
And elements can be accessed singly or as a subset, with 1 being the origin. Parenthesis indicate the indexing operation, and a single index or a range of indexes can be specified.
> a1 [1.1,1.2,1.3,1.4,1,5] > a1(2) 1.2 > a1(1:3) [1.1,1.2,1.3]Since array operations are built into the language, functions applied to the array are automatically applied to all elements at once.
> sqrt(a1) [1.04881,1.09545,1.14018,1.18322,1,2.23607]Arrays are not limited in dimension. The rank (number of indices) of an array is not limited to one (a vector) or two (a matrix), but can be as large as desired. Arrays of rank 3 can be used to represent the distribution of a parameter across a volume, and an array of rank 4 could model this over time.
Yorick also provides a simple but effective help system. Executing the help command describes the help system. Executing it with a command name as an argument provides information on that command.
Yorick provides a complete programming language that closely matches C in terms of control flow, expressions, and variable usage. For example,
> for(i=1; i<10; i++) { print,1<<i; }
print the powers of two just as you would expect, and function declarations, introduced with func, work as expected.
> func csc(x) {
> return 1/sin(x);
> }
There are differences -- variables need not be declared, and arrays are much more powerful than C. The major difference is in function invocation. Passing arguments to a function in parenthesis causes an evaluation and printing of the result, however passing arguments separated by commas simply executes the function and does not return the result. Since in most cases intermediate results are not required, many scripts contain function calls of the form f,x,y rather than the more familiar f(x,y).
Having a programming language close to C allows easy migration between Yorick for prototyping and C for final implementation. However, as several Yorick users have indicated, moving to C was often unnecessary -- the Yorick program proved to be fast enough to get the job done, and with a minimum of programming effort.
If C extensions are required, a straightforward framework allows extending the Yorick command language with whatever new operations are necessary.
Now things get really interesting. Yorick has a compact and sophisticated mechanism for describing array indexing and operations, which are used to precisely specify the desired operation to the interpreter.
As you recall, applying an operation to an array causes the operation to be applied to each element of the array. For example
a = [1,2,3,4,5] sqrt(a) [1,1.41421,1.73205,2,2.23607]
But what about multiplying two vectors? The default is to perform an element by element by multiplication.
b = [2,4,6,8,10] a*b [2,8,18,32,50]
But those of you that remember physics or linear algebra will recall the inner and outer products. The inner product is defined as the sum of the pairwise products:
a(+)*b(+) 110And the outer product creates a matrix out of each possible multiplication
a(-,)*b(,-) [[2,4,6,8,10], [4,8,12,16,20], [6,12,18,24,30], [8,16,24,32,40], [10,20,30,40,50]]
The + and - symbols used where an index would be are called special-subscripts, and provide precise control over how array operations are executed.
The + is the matrix multiplication pseudo-index, which indicates to Yorick along which dimension the addition part of a matrix multiply should be performed.
The - is a pseudo-index, creating an index where one did not exist before.
The operators sum, min, max, and avg can be used in place of indexes.
a(max) 5 b(avg) 6
One might wonder why this is necessary, when the equivalent functional operators (i.e. min() or avg()) exist? The reason is that for matrices of rank more than one, the rank-reducing index operators allow you to specify exactly how to perform the operation. For example, given a 3x3 array, to you want to average across rows, columns, or the entire array?
c = [[1,2,3],[4,5,6],[7,8,9]] dimsof(c) [2,3,3] avg(c) 5 c(avg,avg) 5 c(avg,) [2,5,8] c(,avg) [4,5,6]
Here we have also introduced the dimsof() operator, which reports the dimensions of the argument. In this case the result tells us that c is an array of rank 2, with 3 elements in each direction.
Under Linux, Yorick is linked with the GIST graphics subsystem, allowing immediate display of plots and diagrams. Plots are interactive, allowing the user to zoom in and out, stretch axes, and crop the displays using the mouse. Yorick is capable of displaying sequences of plots over time as a move, and because of this the command to prepare for a new image is fma, or frame advance. Onward.
To plot the value of a function at evenly spaced points we need to first create the x values.
x = span(0,10,256) dimsof(x) [1,256]
X is now a 256 element long array with values that range from 0 to 10.
The plg function, given vectors for the x and y values, plots x-y graphs.
plg, sin(x^2), x
The result is shown in Plot 1. Note that the arguments are supplied y,x (not x,y). This allows Yorick to supply a default x vector (ranging from 1 to the number of y points) if desired.
Parametric plots are also supported. Consider the following code which produces the spiral in Plot 2:
window, style="vgbox.gs" a = span(0,20,256) x = a * sin(a) y = a * cos(a) plg, y, x
Surface plots are also available, either as a wire frame as in Plot 3.
#include "plwf.i" orient3 x = span(-pi,pi,32)(,-:1:32) y = transpose(x) fma plwf, sin(x)*cos(y)
Or a shaded surface rendition as in Plot 4:
fma plwf, sin(x)*cos(y), shade=1, edges=0
A host of advanced graphics options are used in the demonstration programs distributed with Yorick, and the latest copy of the documentation has an extensive description of graphics options. In addition, libraries to read, write, and display PNM format images is provided.
Yorick is an exceptionally rich environment for numerical analysis. Many capabilities such as file IO, debugging, animation, and distributed operation using MPY have been omitted. If you are at all interested please take the time to read through the documentation and the example programs. You will not be disappointed.
Yorick Home Page:
ftp://ftp-icf.llnl.gov/pub/Yorick/yorick-ad.html
Yorick Archive Sites:
ftp://sunsite.unc.edu/pub/Linux/apps/math/matrix/yorick-1.4.src.tar.gz
Linux Software for Scientists (and Curious Layfolk):
http://www-ocean.tamu.edu/~baum/linuxlist.html
Scientific Applications under Linux:
http://SAL.KachineTech.COM/
 Larry Ayers
Larry Ayers Jim Dennis
Jim Dennis Dr. Richard L. Dubs
Dr. Richard L. Dubs Michael J. Hammel
Michael J. Hammel Tom Kunz
Tom Kunz Mike List
Mike List Eric Marsden
Eric Marsden Cary O'Brien
Cary O'Brien Alessandro Usseglio Viretta
Alessandro Usseglio VirettaThanks to all our authors, not just the ones above, but also those who wrote giving us their tips and tricks and making suggestions. Thanks also to our new mirror sites.
Lots of excitement in the air these days what with free Netscape and the debate over OpenSource. We're going through some interesting times.
Well, not much to report this montho on a personal front--work! work! work! makes Margie a dull woman.
Have fun!
Marjorie L. Richardson
Editor, Linux Gazette,
Linux Gazette Issue 26, March 1998, http://www.linuxgazette.com
This page written and maintained by the Editor of Linux Gazette,